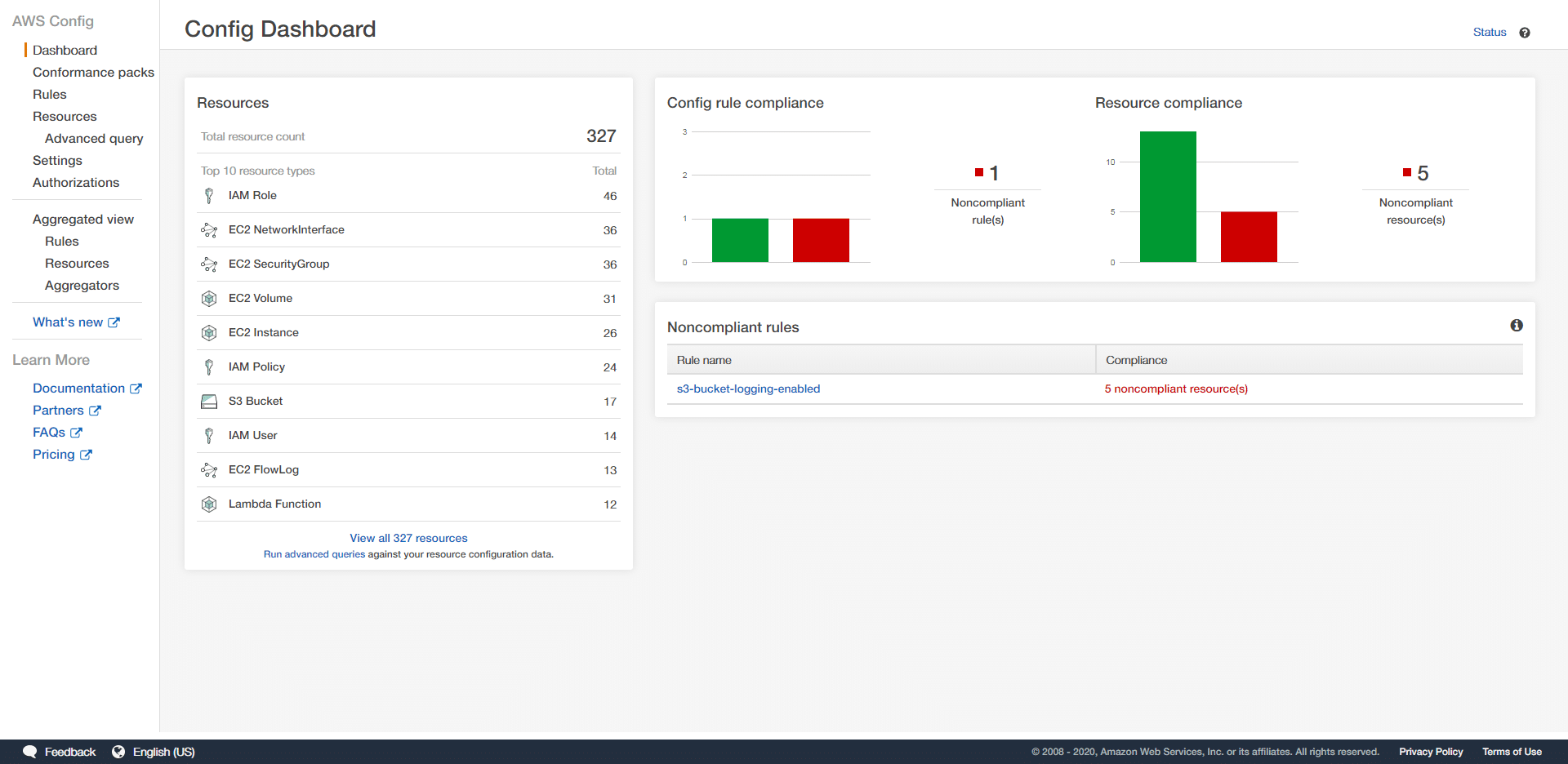
AWS Config is an service for auditing the configuration of resources in AWS. System administrators and security team leaders can use AWS Config to check the actual configuration of their AWS resources, against the desired configuration and uncover non-compliant resources and resources with problematic settings.
AWS Config is very flexible. Your team should ensure that you have properly setup and configured AWS Config rules to gain the most insight from the service. In this article, we introduce a set of best practices that your team can follow when utilizing AWS Config.
Why AWS Config?
When initially starting with AWS, you will only consume a small number of resources. Over time, you will increase resource consumption. You will most likely employ AWS services such as security groups, load balancers, big data solutions, to architect and build solutions within the AWS cloud.
As you scale to hundreds or thousands of resources and build your security programs, you will need to enforce enterprise cybersecurity standards on these resources, but managing this configuration manually is not possible due to the scale of the cloud environment. AWS Config can help you solve this problem.
AWS Config allows your team to define “rules”, that describe the expected behavior of AWS resources. As an example, you can define a rule in AWS Config that checks for a specific security group in EC2 instances. AWS Config will alert you if a new EC2 instance is provisioned without this security group, or if this security group is removed from an existing EC2 instance.
AWS Config has a comprehensive set of predefined rules. You can also create customize Config rules as well. By setting appropriate Config rules, your team can precisely define expected configurations for your AWS resources.
Best Practices For AWS Config
Use AWS Config When There Are Many Users
Setting up AWS Config is a key step for securing your AWS cloud environment when there are multiple users are responsible for managing resources in AWS. For organizations with many users, it is impractical to manually audit all the cloud resources, created by each users.
Enable AWS Config For All Resource Types
When configuring AWS Config either via CLI, console, or CloudFormation stacks, your team should set AWS Config to record all supported resource types. When this option is set, any new resource type provisioned will be automatically added to AWS Config.
If you select only a set of specific resources, AWS Config will not be able to record or audit other types of resources even if your users provision new instances of such resources. This could lead to configuration drift, where new resources have different security configurations then expected. Therefore, it is always recommended that teams enable AWS Config for all resource types.
Use A Secure S3 bucket
AWS Config stores collected findings and data in an S3 bucket. This data includes the configuration history and snapshots. To ensure the security of collected data, this S3 bucket should not be publicly readable or writable. Even within the organization, this S3 bucket should have
permissions granted to only authorized system administrators. When defining an S3 bucket for use with AWS Config, be sure to define an IAM policy that grants least privilege.
Enable AWS Config In All Accounts and Regions
If your organization utilizes multiple AWS accounts, be sure to enable AWS Config in all these accounts. Additionally, if you have resources spread across multiple regions, you must enable AWS Config in all those regions as well. But, for global resources such as AWS IAM, enable AWS Config in one region only.
AWS Config has a feature for aggregating data from multiple accounts and multiple regions. Your team may consider setting up an AWS Config “aggregator” to have one instance of AWS Config collect data across one or more AWS environments. The source account that is enabling AWS Config must be authorized to collect the AWS Config data. Alternatively, if the accounts are part of AWS Organizations, no special authorization is required.
Use CloudFormation Stacks
You can use CloudFormation stacks to configure AWS Config. Your team may consider standardizing AWS Config ruleset deployment by creating specific CloudFormation stacks for further provisioning. It is preferable to use CloudFormation, when there are multiple accounts or regions. As new accounts or regions are added, your team will be able to use the existing CloudFormation templates to enable AWS Config in those new accounts and regions.
Use AWS CloudTrail With AWS Config
AWS CloudTrail can complement AWS Config in cloud administration. To effectively use CloudTrail with AWS Config, you must understand the differences in both services. AWS CloudTrail is a service that records all activities/API events in your AWS accounts. It records all actions executed via CLI, AWS Management Console, AWS SDKs, or any AWS service. CloudTrail stores the collected action logs in an S3 bucket.
A CloudTrail log entry includes the date, time, AWS user, account, region, etc related to any particular action. It also includes the parameters related to the action. As an example, if an EC2 instance that has been stopped was started, the CloudTrail logs include both the previous state and the new state of the EC2 instance. Analyzing CloudTrail logs can help you identify which user executed what activity. CloudTrail logs can also help in troubleshooting problems and root cause analysis.
In comparison to CloudTrail, AWS Config records snapshots of the configuration of AWS resources. Consider the following example:
AWS Config can periodically monitor your WAF ACLs. If AWS Config observes a change that does not comply to one of its defined rules, it will mark this WAF as non-compliant. Then, you need to find out who was responsible for this change. You can find that by analyzing the CloudTrail logs. CloudTrail can help you easily correlate AWS Config non-compliant resources with user activity.
Use CloudWatch Events To Monitor AWS Config
AWS CloudWatch is a monitoring/logging service in AWS. It can collect monitoring data as metrics and events. You can use CloudWatch to monitor the status and health of the resources in AWS.
AWS Config will essentially record snapshots of your AWS resource configuration. It can generate CloudWatch events when a change of resource configuration is detected.
Consider the following example: A user changes a rule in a security group. AWS Config can detect that the rule configurations in the security group have changed. It can also check whether the change is acceptable or not. Then, if the change is violating a defined rule, AWS Config can create a CloudWatch event for it. This allows your team to track AWS Config events/findings and create dashboards within CloudWatch.
Use Amazon SNS For Notifications
Amazon SNS is a messaging service that supports A2A (application-to-application) or A2P (application-to-person) communication. You can use the A2P feature of SNS in combination with AWS Config to notify IT and security administrators of non-compliant configurations.
Teams may consider streaming configuration changes and notifications to an Amazon SNS topic. From this topic, you can send specific events to security team members via email, SMS, or other channels.
Use Conformance Packs
AWS Config can check and verify that your resources comply with a set of policies. These policies are implemented in AWS Config rules. A rule defines the resource type and the checks that should be performed for each type of resource. As an example, you can create a rule that checks whether a specific security group is configured in all EC2 instances in a particular VPC.
Individual Config rules can be manually configured individually via AWS console, CLI, or API. Conformance packs provide an easier way for your team to deploy multiple rules and easily manage them.
A conformance pack is a template in YAML, that defines a set of AWS Config rules. AWS has a set of sample conformance packs. Starting with these samples you can develop your conformance packs more easily than creating individual rules from scratch.
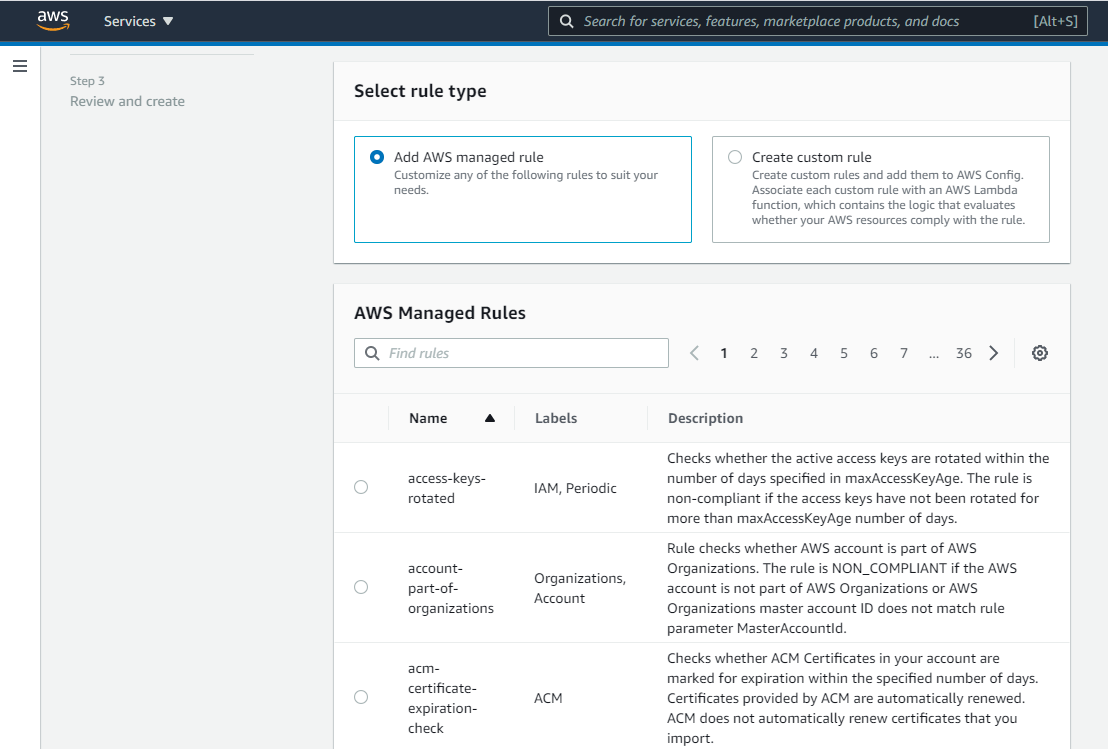
Use Managed Rules As Much As Possible
AWS Config has two kinds of rules; managed rules and custom rules.
A managed rule is a predefined rule that you can readily apply for a resource. AWS Config has a comprehensive set of managed rules. If your team has other parameters that cannot be satisfied by a managed rule, you must create a custom rule.
For creating a custom rule, your team must write a Lambda function with the logic that checks the compliance of the AWS resource. While custom rules are flexible, they can add complexity. Consider using managed rules as much as possible and turn to custom rules as needed.
Use AWS Config RDK For Custom Rules
If you must create custom rules, use the AWS Config RDK (Rule Development Kit). RDK is an open-source Python library provided by AWS. RDK hides some of the complexities involved in custom rule development thus easing the process of rule development.
Enable Periodic Snapshots
A configuration snapshot is a collection of configuration items for AWS Config supported resources that exist in your account. A configuration snapshot provides a picture of resources and their configurations. This configuration information can be delivered to S3 in multiple formats.
In order to gather historic configuration information, your team should configure periodic snapshots in AWS Config to get a snapshot of your resources at least once a day. Implementing this configuration ensures that you have a list of daily snapshots that can help you in troubleshooting configuration activities.
Leverage Dash ComplyOps Security Programs
Dash ComplyOps enables security teams to connect AWS Config rules to security programs and compliance frameworks including SOC 2, HIPAA/HITECH, and ISO 27001. Teams can utilize Dash to implement appropriate administrative policies and connect AWS Config rules and monitoring to regulatory mappings to meet security and compliance needs.
If your team is preparing for client security risk assessments (SRA) or an upcoming security audit, consider using AWS Config alongside Dash ComplyOps in order to build a robust cloud security program.
Conclusion
AWS Config is a useful service for implementing security compliance and inventory for your resources in AWS. It also can help in root cause analysis of certain problems, because you get a historical track record of your resources.
There are multiple ways to configure AWS Config. If you are starting small and scaling up, you may find that your AWS Config setup may become more complicated as new rules are added.
We have described a set of best practices that can help you avoid complexities. These best practices will also help you get maximum outcome from AWS Config while keeping the rule configurations simple and manageable. By following these best practices, you can implement a scalable cloud architecture, to help address enterprise security and administrative policies.



