What Is AWS Config?
AWS Config is an Amazon Web Services (AWS) cloud service that enables teams to manage cloud resource configuration and change management. AWS Config allows teams to evaluate cloud resources against specified configurations.
Since AWS operates on a shared responsibility model, cloud customers are responsible for managing specific security configuration and settings across cloud resources in order to meet security and compliance standards. AWS Config is one service that enables teams to manage and check cloud security configuration. Security teams can leverage AWS Config alongside other security solutions to build and manage their cloud security programs.
Dash ComplyOps Integration with AWS Config
Dash ComplyOps empowers organizations to configure, monitor, and maintain security program in AWS. Security teams utilize Dash to build administrative security policies, enforce policies through continuous compliance monitoring.
The latest integration with AWS Config, enables teams to connect AWS Config security rules into their Dash security programs and manage regulatory and compliance standards controls.
Current Dash customers can utilize the latest AWS Config connection by going to the Dash Action Center and navigating to AWS Config.
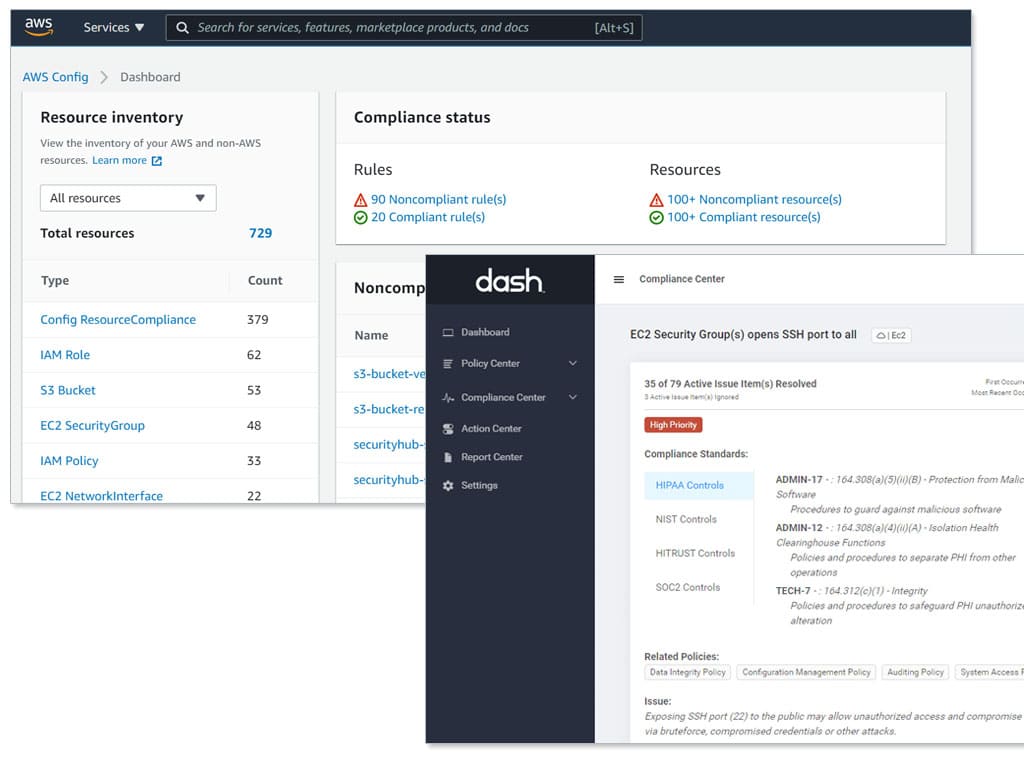
Gathering Compliance Insight from AWS Config
AWS Config rules represent desired configuration settings for AWS resources. When an AWS resource “violates” this rule or does not have the required settings and configuration, AWS Config notifies your team.
AWS Config provides over 100 Managed Config Rules that cloud users can implement out of the box. Some examples include:
- ec2-instance-no-public-ip – Checks whether one or more EC2 instances has a public IP currently available and in use.
- iam-user-mfa-enabled – Checks whether IAM users have multi-factor authentication (MFA) enabled.
- rds-multi-az-support – Checks whether high availability is enabled for your RDS DB instances and multi-AZ deployments.
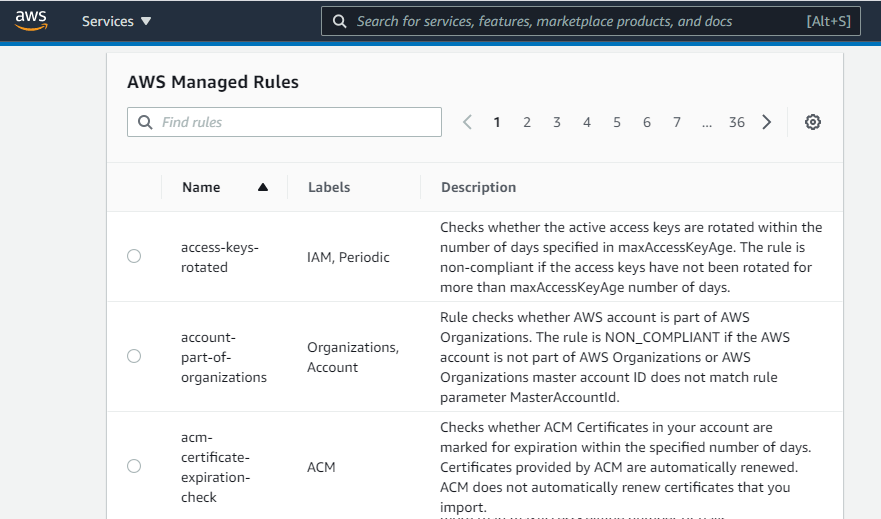
Additionally, teams can create their own custom Config Rules. These rules operate as custom scans and checks and can be created by creating AWS Lambda functions. For example, your team could setup rules related to:
- Confirm cloud resources have specific tags related to provisioning/status
- Check that metadata for resource(s) contains specific configuration
- Check that a specific resource type is used to meet business requirements
Mapping AWS Config to Your Dash Compliance Program
With the latest Dash ComplyOps integration, AWS users can connect AWS Config rules alongside the hundreds of established controls provide by Dash rulesets.
After AWS Config is connected to Dash, your team can view these configuration findings as they relate to compliance frameworks including HIPAA, SOC 2, and HITRUST. Security teams can edit security rule mappings for these compliance standards and build entire security controls inside of Dash.
Example:
AWS Config Rule:
Application Load Balancer(s) (ALBs) are missing HTTP to HTTPS redirection
alb-http-to-https-redirection-check
HIPAA Security Rule Controls:
164.312(e)(1) – Transmission Security – The organization implements measures to guard against unauthorized access to transmitted PHI.
164.312(e)(2)(i) – Integrity Controls – The organization implements measures to ensure integrity of PHI on transmission
164.312(e)(2)(ii) – Encryption – The organization implements mechanisms for encryption of transmitted PHI
SOC 2 Trust Service Criteria Controls:
CC6.1 – Logical and Physical Access Controls – The entity implements logical access security software, infrastructure, and architectures over protected information assets to protect them from security events to meet the entity’s objectives
CC6.7 – Logical and Physical Access Controls – The entity restricts the transmission, movement, and removal of information to authorized internal and external users and processes, and protects it during transmission, movement, or removal to meet the entity’s objectives.
Dash effectively connects AWS Config rules to compliance framework standards and enables your team to easy manage, and inventory security controls across your cloud environments.
Building Your Cloud Security Program
Security and DevOps teams managing workloads in AWS can leverage Dash ComplyOps and services including AWS Config to quickly build a security program using controls from multiple cloud sources.
Dash has been purpose built for the AWS Cloud and makes it easy for your team to build and manage a cloud native security program with limited overhead.
Benefits of Dash:
- Gather security events and findings across all cloud resources and security sources.
- Manage security issues, resolution in one place
- See security findings as they relate to compliance standards including – HIPAA/HITECH, SOC 2, and NIST
- Easily prepare for security audits, risk assessments, and client questionnaires
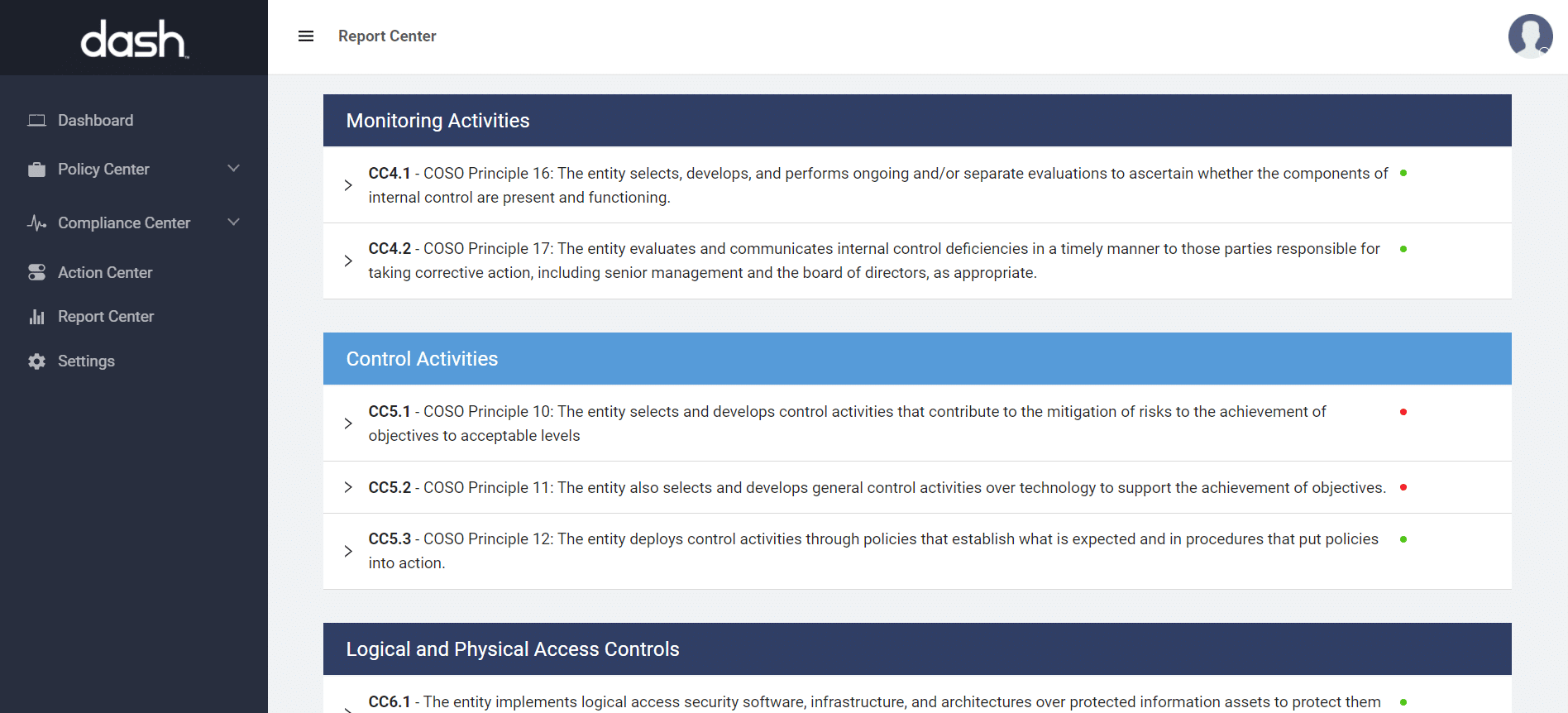
Streamline Compliance with Dash ComplyOps
Dash ComplyOps makes it easy for teams to develop a robust AWS Compliance Program and meet security and compliance standards including HIPAA, SOC 2, HITRUST CSF. Dash enables teams to streamline security audits, easily answer client risk assessments, and are much better prepared to manage security programs within their organization.
Learn how Dash can help your team automate your AWS security program, set and enforce cloud security standards and enforcement. and save hundreds of hours each year. Get started with a 7-day free trial of Dash.


