AWS Cloud Security Auditing
Organizations must manage security safeguards when managing production workloads in AWS. Learn about tools for AWS security scanning and auditing.
Auditing AWS Account Security
When running infrastructure in the AWS Cloud it is important to ensure that cloud services and IT resources are securely configured and meet any compliance standards. Most public cloud platforms, including AWS operate on a Cloud Shared Responsibility Model, meaning that cloud customers are responsible for specific security configuration in the cloud. Teams should be performing cloud security audits to find security issues and potential gaps in existing cloud security plans.
While organizations typically have established security programs, it is important for DevOps staff continually monitor and confirm that all cloud services have all necessary security configuration, permissions, rules, and policies. Teams may leverage specific AWS audit tools and AWS security scanning tools such as Dash ComplyOps to examine cloud environment and gain better insight into cloud security issues.

Download Out Guide To Architecting For Cloud Compliance
Identifying Potential Cloud Service Issues
With the many security options provided by AWS teams must be careful and guarantee that security protections are maintained across all services. Cloud misconfigurations could lead to a potential security breach of the cloud environment. Teams should perform AWS auditing to identify common threats to AWS cloud services including the following types of security issues:
Permissions/Access Issues
Teams with improper IAM users, roles, and permissions are at risk of privilege escalation and unauthorized access.
Network Issues
AWS enables organizations to configure numerous network security settings. Teams with insecure networking settings for VPCs, Security Groups, and NACLs could end up with vulnerable network.
Availability Issues
Organizations managing production workloads on AWS typically build for high availability. Cloud service issues related to load balancers, NAT gateways and issues with fail-over could lead to a potential service outage.
Data Loss Issues
Individual cloud services with improper security controls may be vulnerable to hacking and may be accessed by unauthorized third parties.
Compliance Issues
Regulatory compliance standards such as HIPAA and cybersecurity standards such as SOC 2 require teams to maintain specific security standards for IT infrastructure. Missing protections, or changes to security configuration could lead to non-compliance.
Building Secure and Compliant Applications?
Performing An AWS Cloud Security Audit
Organizations managing production applications in Amazon Web Services must configure specific security settings across cloud services in order to maintain cloud security. Security teams and DevOps staff should have security policies in-place and conduct security auditing for AWS cloud infrastructure. Organizations may consider utilizing a tool such as Dash ComplyOps to automate the security auditing process.
1. Inventory Cloud Resources and Services
Security teams should take an inventory of all cloud services and resources that are in use within your AWS cloud environment. These resources need to be identified before evaluating cloud security standards.
2. Identify Cloud Security Issues
After identifying cloud resources, your team should perform security scanning for cloud security issues within AWS resources. Each individual AWS service has different security configuration, so it is important that your team identify security issues that may be specific to certain cloud services.
3. Remediate and Resolve Cloud Security Issues
Once security issues are identified in your AWS cloud environment, your team should work with DevOps staff to make changes to your cloud configuration and resolve security issues.
5. Review and Update Security Policies
Teams should periodically review and update security policies and standard operating procedures in order to meet new security standards and eliminate potential security program gaps.
AWS Cloud Auditing With Dash ComplyOps
Dash ComplyOps provides teams with a solution for building and monitoring security programs in Amazon Web Services. ComplyOps enables organizations to create robust cloud security policies and security programs and then enforces polices through compliance monitoring. ComplyOps provides AWS security scanner functionality and allows teams to find and resolve potential security and compliance issues.
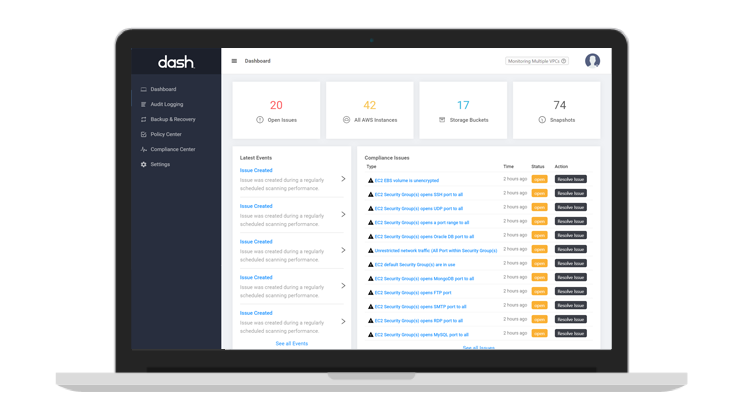
Dash Security Findings
Dash provides teams with monitoring and AWS security auditing of your AWS cloud environment. Teams can automatically scan services such as EC2, RDS, and S3 for cloud configuration issues.
Dash provides security findings and allows your team to identify cloud security issues such as:
- Security Groups with open SSH/FTP/DB ports
- VPCs allowing all ingress/egress traffic
- Subnets without flow logs
- RDS instances with unencrypted storage
- IAM policies allowing NotActions
- S3 buckets that are world readable/writable
- Redshift clusters with activity logging disabled
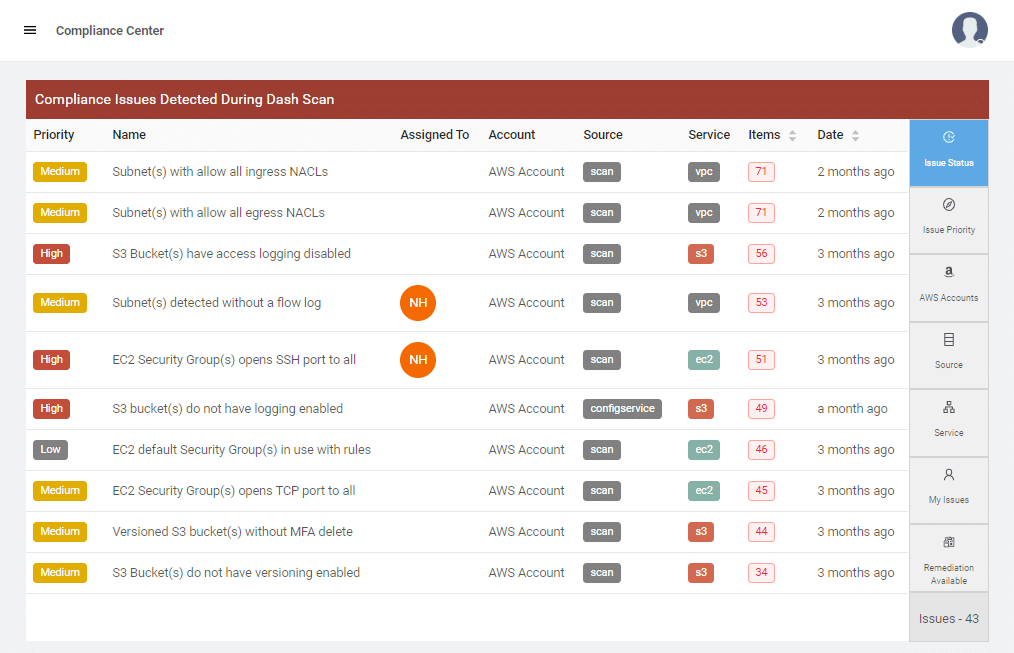
Automated Cloud Security Auditing
Dash continuous compliance monitoring provides teams with automated security scanning of your AWS cloud environments. Dash identifies security issues within individual AWS services such as Amazon EC2, S3, RDS and IAM and provides steps for remediating cloud issues. Unlike traditional single point-in-time audits, teams can use ComplyOps to continually audit and monitor cloud security issues and ensure the integrity of your cloud security posture.
Streamlined Compliance
Dash security policies and cloud scanning is built around HIPAA, HITRUST and SOC 2 compliance standards, so your team can easily manage regulatory compliance in AWS. Each security scan is mapped to compliance standards so your team can see determine your state of compliance in AWS. Dash makes it easy to develop a robust cloud compliance program and enforce security standards across AWS resources to meet compliance requirements.
AWS Security Reports
Dash cloud security reports provide security teams with a solution for validating cloud security efforts. Teams can utilize AWS cloud security reports to see security safeguards, determine gaps and help teams answer security risk assessments (SRAs).
Cloud Native Security
Dash is built for AWS cloud environments. Teams can deploy the Dash application via the AWS Marketplace and can leverage specific AWS security tools such as AWS GuardDuty to extend the security and capabilities of Dash ComplyOps. Dash operates as a true nerve-center for AWS security and compliance.
Monitor and Audit AWS Security
Automate AWS security auditing and manage security and compliance