SOC 2 vs ISO 27001, Which One Do You Need?
Differences between SOC 2 and ISO 27001 security certifications. Learn about the requirements and overall benefits of SOC 2 Type 1, Type 2, and ISO 27001. See which attestation is best for your organization.
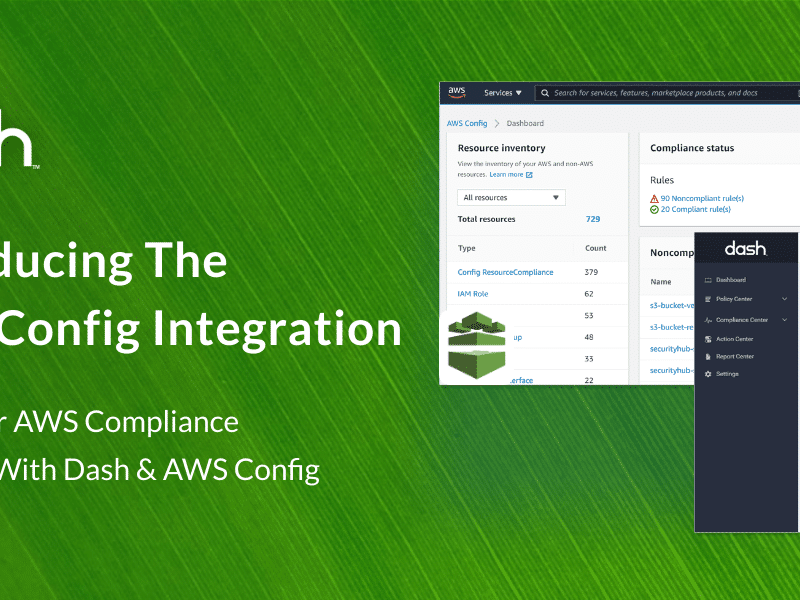
Introducing Dash ComplyOps Integration With AWS Config
Dash ComplyOps has integrated AWS Config. Teams can connect AWS Config rules to Dash to build HIPAA, SOC 2, and HITRUST security controls, and manage your compliance programs in AWS.
How Startups Can Achieve SOC 2 Compliance
A SOC 2 report is an effective way to demonstrate the security posture of your startup organization to potential clients. Learn about SOC 2 certification benefits and learn about achieving compliance in 3 steps.
The HIPAA Security Rule
The HIPAA Security Rule outlines technical requirements needed in order to meet HIPAA compliance. Learn about your organization’s responsibilities and see the HIPAA Security Rule checklist.
HIPAA Compliance Checklist
HIPAA compliance checklist for building compliant applications and cloud solutions. Learn about HIPAA compliance standards and see steps and safeguards required to become compliant.
10 Common Questions Around SOC 2 Compliance
SOC 2 can be a complicated security standard to understand. Learn more about the basics of SOC 2 compliance and how teams become SOC 2 compliant. Read a general overview of SOC 2 assessment framework and frequently asked questions.
How To Select a SOC 2 Auditor
SOC 2 audits can only performed by an AICPA affiliated firm. Learn about requirements and best practices for selecting a SOC 2 Auditor, performing assessment, and receiving SOC 2 reports.
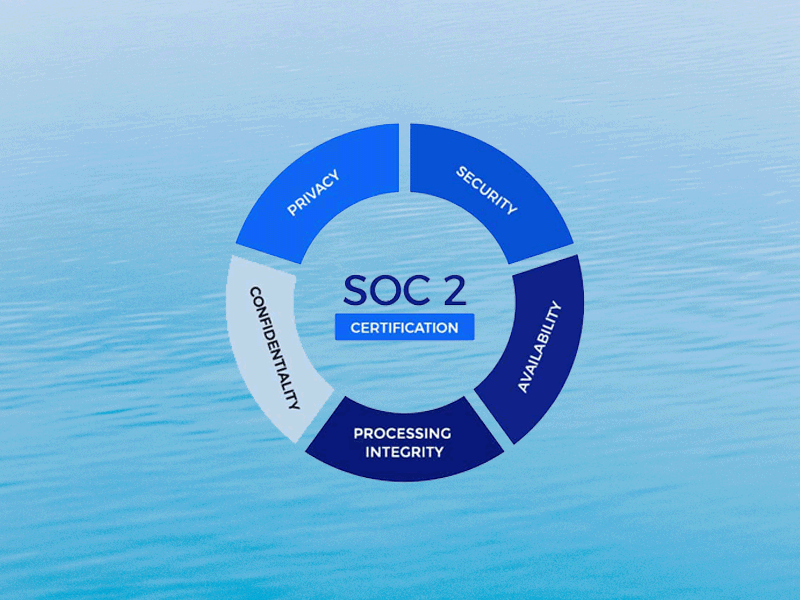
SOC 2 and The Trust Services Criteria (TSC)
SOC 2 evaluates teams based on set of controls defined in the Trust Services Criteria (TSC). Learn about the 5 categories of security controls and requirements for SOC 2 compliance.
Overview of SOC 2 Reports
Learn about SOC 2 reports and how organizations achieve SOC 2 Type 1 and SOC 2 Type 2 reports. See the steps to achieving SOC 2 compliance and getting a SOC 2 report.
Achieving Disaster Recovery Compliance for AWS Workloads
Disaster recovery (DR) is a requirement for most regulatory standards and cybersecurity standards. Learn about potential data disaster scenarios and disaster recovery requirements for maintaining compliance in AWS.