NIST 800-53 Compliance Automation
Build and manage your NIST 800-53 security program. Fulfill NIST core functions in the cloud.
Book A Demo
Get Started with Dash ComplyOps compliance automation
Managing NIST CSF and NIST 800-53 In AWS
Security teams managing cloud security and compliance often turn to a cybersecurity framework like NIST Cybersecurity Framework (NIST CSF) and NIST 800-53. While AWS has been independently validated against the NIST 800-53 Revision 4 controls, security and compliance is ultimately a shared responsibility between AWS and the cloud customer.
Under the AWS cloud shared responsibility model, AWS is responsible for many of the physical and administrative security standards, such as managing access to physical servers, managing third-party vendors, etc. It is up to cloud customers to ensure that administrative policies are implemented, and cloud services have proper security standards including backup and disaster recovery, audit logging, and intrusion detection. Dash ComplyOps makes it easy for teams to manage NIST security responsibilities.


Custom Compliance Policies
NIST compliance requires that organizations set administrative policies and address safeguards including creating security roles, performing risk analysis, and managing incident response. Dash enables teams to generate custom compliance policies based around on your organization’s needs, structure, and technologies. Policies are designed around Amazon Web Services and customized through easy to answer questions.
Learn More About Administrative Policies
Technical Security Controls
Dash establishes a set of cloud security controls based NIST baseline requirements and your organization’s established policies and procedure. Controls are built around individual AWS cloud services, best security practices, and NIST standards. Organizations can utilize Dash “click-to-fix” remediations to solve compliance issues with one click and maintain technical security standards.
Learn More About Technical Controls
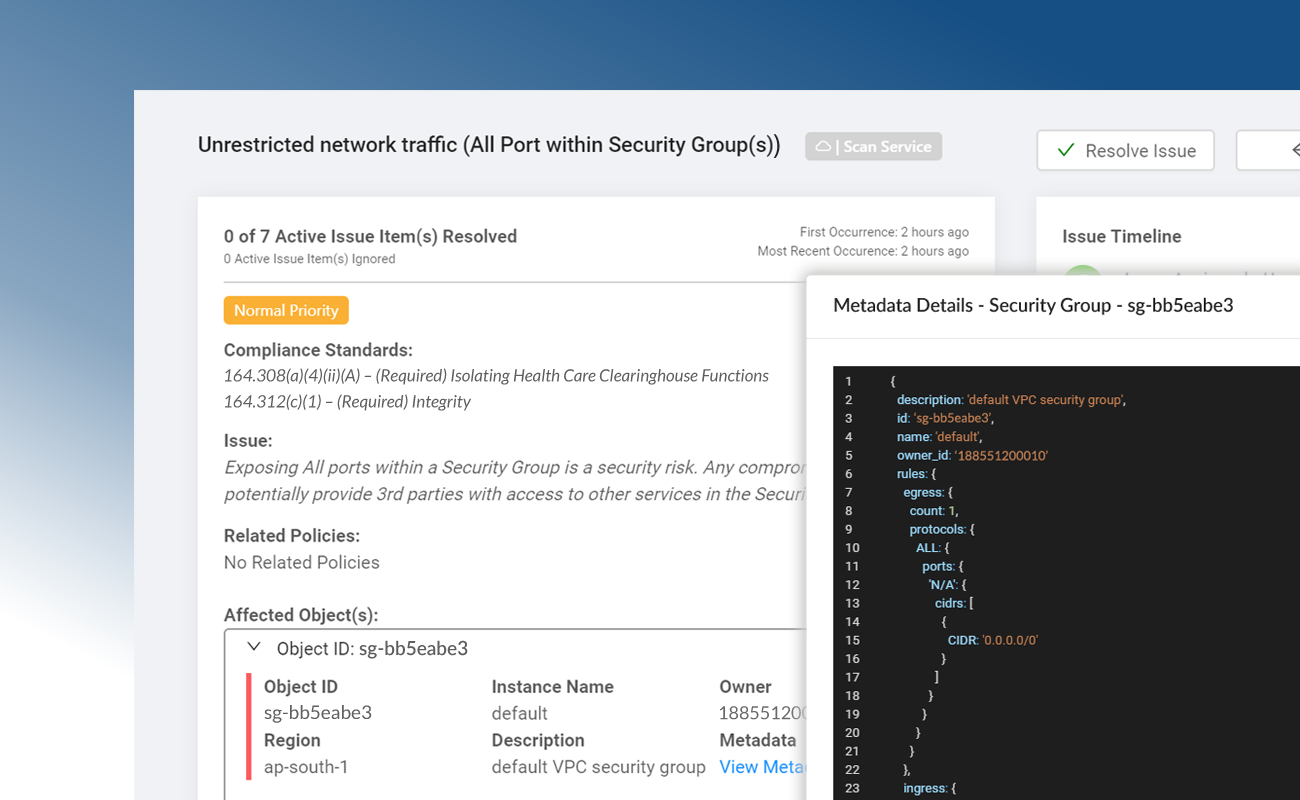
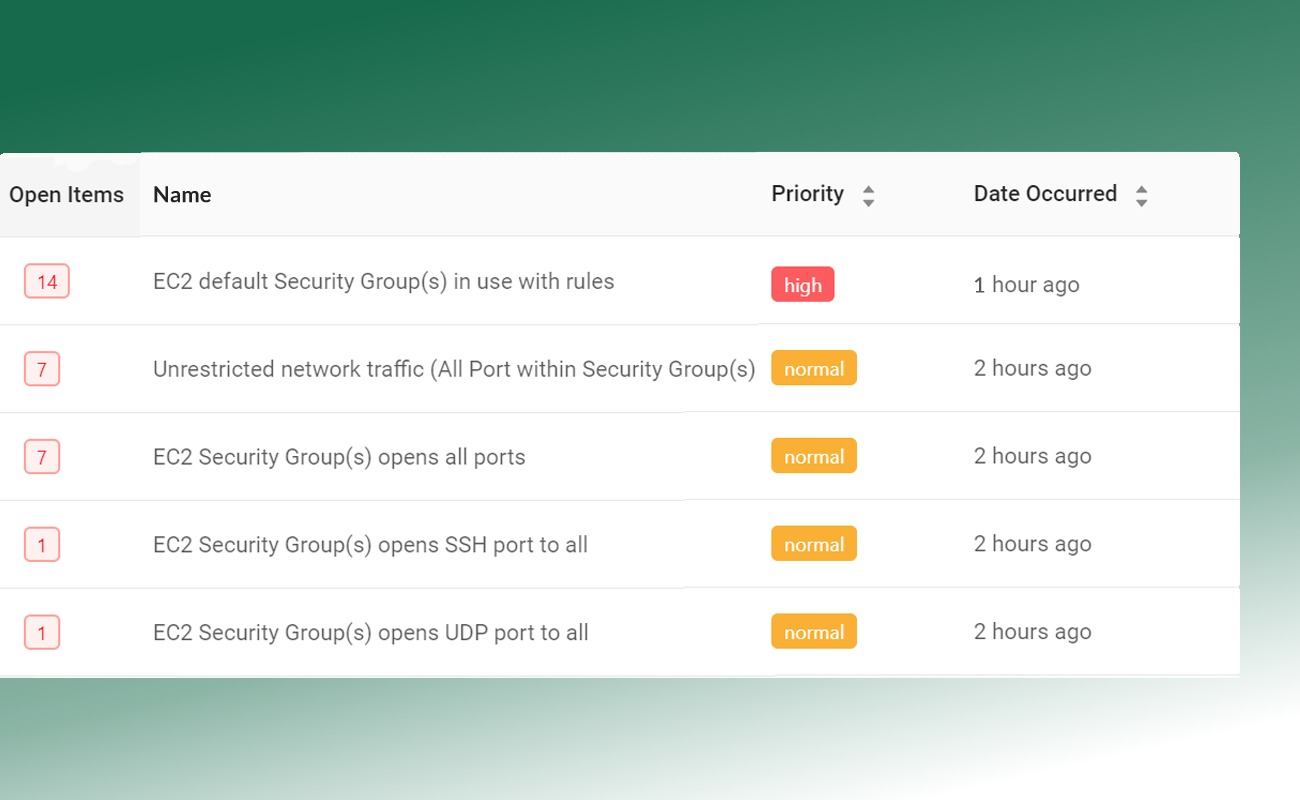
Continuous Compliance Monitoring
Dash continuous monitors your AWS accounts for NIST configuration and security issues. Dash detects compliance concerns in your cloud environment such as unencrypted EBS volumes, audit logging issues and S3 buckets that are open to the public, alerts your team, and provides steps for resolving issues before they become security incidents. Security issues are mapped to NIST publications and NIST 800-53 standards.
Learn More About Continuous Compliance Monitoring
Get Started With AWS Compliance Automation.
Address NIST CSF Functions In AWS
Dash enables teams to build and implement compliance controls around NIST core functions.
Identify (ID)
Developing an understanding for managing cybersecurity risk to systems, people, assets, data, and capabilities. This function includes identifying physical and software assets, cybersecurity policies, asset vulnerabilities, and risk management strategies.
Protect (PR)
Developing and establishing appropriate safeguards to ensure delivery of critical infrastructure services. This function outlines protections such as implementing Identity Management and Access Control, staff awareness and training, data security protection, and protections to ensure system availability and security.
Detect (DE)
Planning and implementing appropriate solutions to identify the occurrence of a cybersecurity event. This function outlines continuous security monitoring, event collection, and activities for enabling the discovery of cybersecurity events.
Respond (RS)
Building incident response procedures and managing activities around cybersecurity incidents. This function outlines incident response planning, communication, incident analysis and mitigation.
Recover (RC)
Building and managing recovery standards for restoring services after a cybersecurity incident. This function outlines standards for restoring capabilities or services that were impaired due to a cybersecurity incident.
Manage NIST CSF and NIST 800-53 in AWS
Fulfill NIST 800-53 Functions In AWS
Dash enables teams to plan and implement compliance safeguards and security controls including the following
Risk Assessment (ID.RA)
Dash provides administrative policies, security monitoring, and task tracking for risk analysis and risk assessment, so security teams to understand understands potential cybersecurity risks.
Governance (ID.GV)
The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk.
Security Continuous Monitoring (DE.CM)
Dash Continuous Compliance Monitoring scans cloud assets and information system at discrete intervals to identify cybersecurity events and verify the effectiveness of protective measures.
Identity Management, Authentication and Access Control (PR.AC)
Dash security controls, together with AWS Identity Access Management (IAM) restrict system access to only authorized users, roles, and applications. Services access is restricted to avoid unauthorized access.
Information Protection Processes and Procedures (PR.IP)
Dash security policies dictate security roles, responsibilities, processes, and management of security protections for systems and assets.
Data Security (PR.DS)
Dash confirms that AWS services are configured with proper protections including networking, encryption, and backup. Safeguards are implemented to protect the confidentiality, integrity, and availability of information.
Response Planning (RS.RP)
Dash provides policies around incident response and disaster recovery (DR), to ensure timely response to detected cybersecurity events.
Recovery Planning (RC.RP)
Dash backup and disaster recovery (DR) standards ensure that cloud services have applicable backup settings. Established procedures ensure timely restoration of services.
Want To Learn More About Compliance Automation
Ready To Get Started With Dash ComplyOps?
Dash ComplyOps
AWS Security Automation
Dash ComplyOps empowers teams to configure, monitor, and maintain robust security controls across AWS cloud environments.
7-day risk free trial.
7-day risk free trial