Preparing For A Hospital Risk Assessment
Handle security questionnaires and vendor risk assessments
Hospital Vendor Assessments Overview
Healthcare vendors, software companies, and digital health companies that collaborate or sell solutions to Healthcare Providers typically run into a Vendor Security Assessment or “Security Questionnaire” when going through procurement. Hospitals utilize vendor assessments to gauge the potential security and compliance risk of solutions, as well as understand how solutions will fit with other systems.
Once a health provider enters into an engagement with a healthcare vendor, a Business Associates Agreement (BAA) is typically signed and health providers have a certain level of liability for all of the vendors they utilize. For healthcare vendors and software companies that plan to sell into hospitals, it is critical that the company has established a proper security plan with proper policies and procedures for addressing HIPAA compliance and general security practices. Having a robust security program simplifies vendor assessments and eases provider concerns.
See our guide to preparing for vendor risk assessments and checklist.
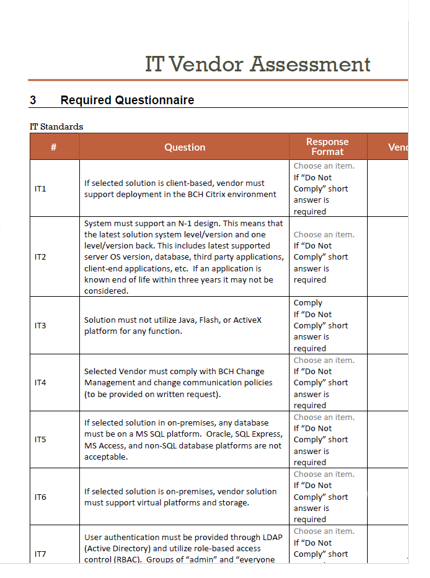
Health Providers Evaluate Many Categories
Healthcare providers use vendor risk assessments to determine the risk vendors pose to the organizations. Providers measure a number of categories to determine how effective a team’s security program is. Assessments may include questions around:
Administrative Policies
Your organization’s set security policies and standard operating procedures.
Regulatory Compliance
Your organization’s compliance with applicable regulations such as HIPAA/HITECH, FDA, etc.
Technical Security Standards
Your organization’s encryption standards, disaster recovery plans, etc.
Cloud Configuration
Your organization’s cloud technologies, structure, and security configuration.
Business Associates’ Agreements (BAAs)
Your organization’s agreements and management of protected health information (PHI).
System Architecture
Your organization’s technology stack and it’s compatibility with the provider.
Support Structure
Your organization’s available support plans, services, and overall service level agreements (SLAs).
Staff & User Roles
Your organization’s employee policies and defined user roles and permissions.
Preparing for Vendor Assessments
Your organization should have administrative policies in place that are understandable – Healthcare vendors that do not understand their own policies are less likely to follow those policies. Your team should set policies that match your organizations technologies and staff structure.
Your safeguards for review, assessment, and technical controls should be realistic – If you are an organization of 5 employees, it may be hard to conduct penetration testing on a monthly basis. Healthcare providers want to see a security plan that a vendor will execute on.
You should have a plan for ongoing assessment of security and compliance – Security and HIPAA compliance are not one-time items. Healthcare providers look for vendors that have policies and procedures for continually assessing security concerns and remediating issues.
Your organization should address general security best practices – For more technical staff want to see that organization how to handle the basics of cybersecurity and required technical controls such as encryption, backup and disaster recovery, auditing, firewall/network security.
Preparing Your Compliance Package For Hospitals?
Get Our Guide To Preparing For Vendor Assessments.
Leveraging Dash for Answering Vendor Assessments
Dash makes it easy for teams to establish a robust security program and answer hospital vendor assessments. Dash provides compliance reports and numerous features for proving and validating compliance.
Custom Administrative Policies
Create administrative policies by answering plain-English questions. Policies created in Dash are tied into technical controls and further event reminders.
Continuous Compliance Management
Dash continually scans your AWS cloud environment for HIPAA regulatory issues. Scans are based HIPAA safeguards, client policies, and best security practices for each individual AWS cloud service.
Instant Compliance Notifications
Receive reports and compliance issue emails and slack messages when your organization has regulatory issues. Dash provides recommendations and remediation for HIPAA compliance events so your organization can avoid falling out of compliance.
Cloud Focused Compliance
Build on Amazon Web Services, the market-leading public cloud platform, without having to deal with the burden of HIPAA regulatory compliance.
Are You Prepared For A Security Risk Assessment?
Prepare for hospital vendor risk assessments and security questionnaires.