With over 100 HIPAA-eligible services, Amazon Web Services (AWS) lends itself to healthcare innovation. However, no AWS service is automatically HIPAA compliant. AWS operates on a shared responsibility model, meaning that Amazon provides an architecture that can be adapted to meet HIPAA requirements by customizing controls and policies. In this post, we’ll break down what “shared responsibility” means in AWS, discuss key challenges to continuous compliance in AWS and their solutions, and outline the four steps to follow when building a HIPAA compliant AWS environment.
What is Continuous Compliance?
According to HIPAA, the legislation that safeguards protected health information (PHI and ePHI), organizations that come into contact with PHI and ePHI are required to take sufficient measures to secure this data from breach or misuse. HIPAA requires a baseline of controls for access control, authentication, data protection, infrastructure, monitoring, audit logging, and incident response for all environments hosting ePHI.
When using a cloud service provider to host patient data, there are three important compliance considerations:
- Physical security of data warehouses and cloud services
- Administrative controls and policies for managing ePHI
- Technical security of the ePHI you collect, store, or transmit
Additionally, you will need to sign a Business Associate Agreement (BAA) with your cloud provider.
What Does Compliance Mean in AWS?
AWS offers HIPAA-eligible services within a shared responsibility model. Amazon provides a BAA, which creates a legal responsibility on the part of both parties to protect PHI/ePHI according to HIPAA standards. Beyond this, AWS is responsible for security of the cloud (data centers). Security in the cloud (cloud resources, infrastructure, applications) is your responsibility as the customer.
To achieve continuous compliance in AWS, teams should build administrative policies and set standard operating procedures (SOPs) based around necessary compliance frameworks. These policies should outline how security controls and technical safeguards are implemented and maintained across the cloud. You must then implement technical safeguards for all cloud assets and instances. Without proper security configuration, your AWS environment may be vulnerable to security breaches and ePHI may be compromised.
The specific requirements for HIPAA compliance vary depending on the service. For example, if you’re using hosted services such as Amazon S3 or DynamoDB, AWS secures the infrastructure, the operating system, and the platforms themselves. The customer, on the other hand, must encrypt all data, classify assets using tags, and apply permission groups (limiting which users can access ePHI) using Identity and Access Management (IAM) tools. Each service also comes with its own unique configuration and encryption requirements. In DynamoDB, connections containing ePHI may only use endpoints that accept encrypted transport (HTTPS). In AWS Volume Gateway, meanwhile, customers should attach local disks in a particular way and cache according to their own security compliance policy.
A full list of all AWS HIPAA-eligible services and their configuration requirements can be found here.
Challenges of Compliance

Continuous compliance in AWS (and any cloud provider) is a mindset as much as a set of tools or policies. Continuous compliance assumes that compliance is a daily, proactive process as opposed to a reactive one.
Maintaining continuous compliance in AWS demands continuous work from the cloud customer. To keep your cloud environment HIPAA compliant, you need to design, implement, and document policies and security controls for all your instances and assets. You also need to manage any changes to these resources and policies. This is where AWS security monitoring becomes essential.
Because new data and cloud resources are constantly being created, you’ll want to establish policies and processes that can scale with your business. Continuous compliance can be achieved only when your processes are:
- Scalable
- Repeatable
- Reliable
- Consistent
DevOps team members responsible for security configuration in the cloud often manually implement regulatory compliance and security configuration in the cloud. Manual compliance management is neither reliable nor consistent because of the risk of human error inherent in spreadsheet tracking of compliance policies, processes, and resources. Another problem with manual compliance management is that a gap quickly grows between your infrastructure security goals and the reality of your environment. As your infrastructure grows, this gap only increases. The biggest danger of manual monitoring, however, is that your organization will only become aware of a compliance issue when the individual responsible for compliance completes a security check, not at the time the issue occurs. This lag time increases the odds that a gap in security will be leveraged by hackers to steal your ePHI.
For these reasons, automation and AWS monitoring is an essential piece of any continuous cloud compliance strategy. AWS provides a useful in-house compliance management tool, Identity and Access Management (IAM), to create user roles and permissions. Other automation tools can be added on top of this to manage your compliance via customization of controls and security monitoring. These tools provide essential safeguards for preventing breaches and HIPAA penalties that come with them. Dash Continuous Compliance, monitors your cloud environment around the clock and notifies your security team as soon as cloud compliance issues are detected.
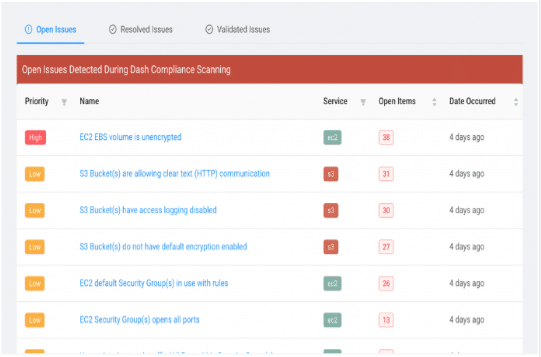
In addition, Dash also automatically issues reports and provides the validation needed for tackling HIPAA risk assessments, ensuring full documentation.
Compliance in 4 Steps
- Determine what assets you have and what the compliance requirements are for each of them. First, you should conduct an inventory of your cloud environment to identify which cloud resources, infrastructure, and applications come into contact with ePHI. Next, you should determine what the appropriate regulations and policies are for each particular AWS service.
- Translate regulations into security policies, and implement controls to meet compliance requirements. Administrative policies should be created by the organization and outline implementation of cloud security controls to meet regulatory standards. Security teams and DevOps staff must implement security controls for individual cloud services. Cloud security controls must be checked regularly to confirm that there are no security issues.
- Identify and document controls owned by third parties and verify that your security objectives are being met. According to HIPAA, you can be held accountable for breaches by a third party to which you entrust ePHI. While a BAA helps insulate you from the legal repercussions of a business associate’s negligence or wrongdoing, the easier scenario is to eliminate this possibility upfront. Additionally, you will need to be able to document due diligence in your third-party relationships in case of a HIPAA audit.
- Continuously assess and update the security of your cloud environment. Once you’ve implemented the necessary policies and security controls, your team should be continuously reviewing your environment to identify issues or possible breaches. This is where an automated compliance management solution is irreplaceable. With manual processes, a compliance issue can go unnoticed for days or even weeks, giving hackers an open door to steal your ePHI.
Conclusion
AWS is a HIPAA-eligible platform; it is not compliant out-of-the-box. It is up to your CTO, HIPAA Security Officer, and IT team to secure your AWS services, maintain security safeguards, and document compliance. The first step in this process is determining what elements of your cloud environment come into contact with ePHI and what the safeguards are required for each service. Next, you need to translate those regulations into clear security rules for your assets and instances, and then confirm the steps that third-parties are taking to secure your data on their end.
The last step in AWS continuous compliance is monitoring your environment to detect issues and breaches. Organizations that do this manually put themselves at huge risk for having undetected, costly breaches. Best-practice is automating all aspects of your cloud compliance, and implementing AWS monitoring to reduce human error and maintain round-the-clock visibility.
Dash is a leading HIPAA compliance solution for cloud-based healthcare organizations, software vendors, and application developers. To learn more about how Dash can help you get continuously compliant or to request a free demo , get in touch with us.
Download Guide To Automating Compliance
A practical approach to building and architecting for continuous compliance in the public cloud.


