What is IAM?
Amazon Identity Access Management (IAM) is AWS’s cloud service for managing access control across AWS cloud services. Cloud users can use IAM to set user permissions and access and define what permissions for cloud services and roles. Since IAM is provides many options for customization, organizations must configure and review IAM follow the rule of least privilege, especially when building security programs and managing compliance.
Cybersecurity frameworks such as the NIST and ISO, as well as regulatory frameworks such as HIPAA, PCI DSS require that organizations implement specific access control safeguards. Teams may implement access control for operating systems and applications but must also safeguard cloud data and cloud platform access. Security teams may consider using Dash continuous compliance monitoring to automatically detect and resolve security concerns in IAM and other AWS services.
Below are a some of the steps that security teams should take when managing IAM permissions in AWS:
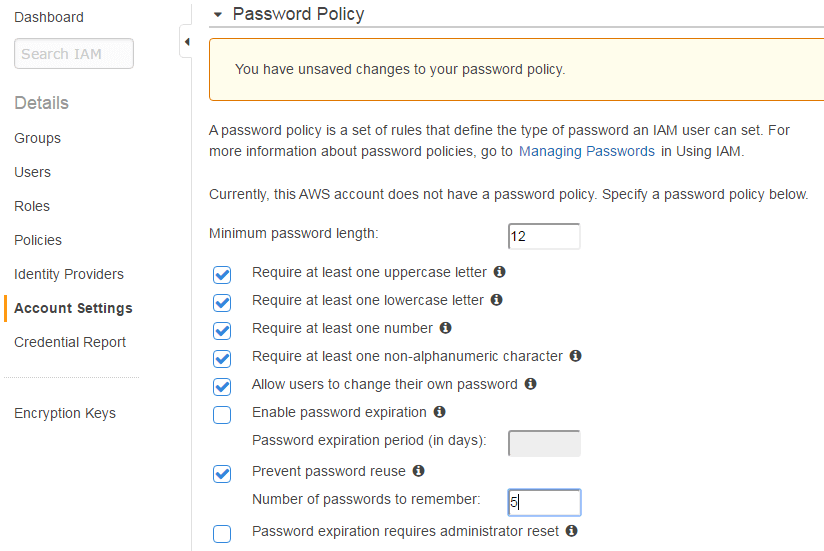
Set a Strong Account Password Policy
Set Password Rotation Period: In order to avoid using compromised credentials, teams should reset (rotate) user passwords every 90 days or more often.
Set Password Strength Requirements: IAM allows teams to set character requirements for user passwords such as minimum length, number of numbers, special characters, etc. Organizations should set a strong password length and require a certain amount of complexity for passwords.
Set Password Reuse Limits: Organizations should limit how previously passwords may be used for future passwords.
Enable multi-factor authentication (MFA): For high privileged users, multi-factor authentication should be enabled for extra protection. Organizations should consider implementing MFA for users with access to production systems and other dangerous operations.
Restrict AWS Root Account Access
When first signing up for AWS, organizations will have a route account associated with their email. Root account provides full access to your AWS cloud resources and billing information. Organizations should create scoped IAM users and immediately avoid using this root account when performing cloud actions. Utilizing IAM users will allow teams to better limit permissions and log activity for auditing purposes. Root accounts should be protected with strong passwords and multi-factor authentication to protect their integrity. Any access keys associated with root accounts should be deleted.
Rotate IAM Access Keys
Users and applications utilize IAM access keys for programmatic access to cloud services. These access keys are connected to the IAM permission set of the user, meaning that any compromised keys may be used to access to conduct security events in your AWS account.
Users should protect these access keys and never share them with others. In the IAM password policy, organizations should define an access key rotation (reset) period, to avoid keys from becoming compromised. Access keys should be deleted for users where they are not used.
Avoid “Administrator” and “Full-Access” Permissions
AWS provides teams with pre-defined sets of policies for IAM permissions. High privileged roles such as “Administrator-Access” and “Full-Access” are very easy for admins to turn on and provide to users, but should be avoided. Instead organizations should build permission sets around only necessary permissions needed to conduct daily operations. Security teams and DevOps staff should not plan on defining escalated permissions and then coming back to edit permissions “later”.
Assign Permissions At IAM Group/Role Level
AWS allows teams to assign IAM permission to individual users using in-line policies. Teams may also create IAM groups with permissions that may be used for multiple users and roles. Building IAM groups, allows organizations to define a standard set of permissions for a specific role or purpose (such as Developer roles, DevOps, etc). Groups are easier to manage and allow teams streamline permissions for multiple users and roles. Organizations should consider building and attaching permissions to IAM groups and rather than attaching permissions on the individual IAM user level.
Avoid Shared Users and Remove Temporary Users/Roles
Organizations should avoid creating any IAM identities that are shared between staff or entities. All staff members with cloud access should have separate user credentials, so that organizations can define permissions for individual staff members and track individual user activity for audit logging purposes.
Any IAM Users or Roles that are defined for testing or development purposes should have limited permissions and should be removed when not needed. Organizations should remove temporary users when reviewing IAM settings.
Use IAM Roles for Applications Running on Amazon EC2
Applications that require access to other AWS services will need their own credentials. AWS allows teams to attach IAM roles directly to EC2 instances in order to apply permissions to them. Roles can have their own set of permissions without any users/groups needing to be attached to them. This is the easiest to apply and manage permissions for EC2 instances.
Collect User Activity Logs
Organizations should turn on logging for IAM users and cloud platform activity by enabling CloudTrail. Enabling these logs allows AWS to automatically log events such creation, modification, or deletion of resources. Security teams should collect events and review audit logs for suspicious behavior. Teams can also use these logs to better see how permissions are being used with users and then change permissions to meet security needs.
Periodically Review User Permissions
Organizations should plan on reviewing IAM permissions on a periodic basis. All security concerns should be shared with appropriate staff and resolved in a timely manner. When reviewing IAM configuration, organizations should manage the concerns including:
- Confirm that IAM password policies are set that high security practices.
- Remove IAM users/access keys for staff and entities no longer working with the organization.
- Remove IAM users that have been inactive for over 120 days.
- Remove individual permissions for users where roles and responsibilities have changed.
- View cloud access logs for suspicious behavior.
Reviewing IAM settings will allow your team to keep a more have better control of your organizations cloud security.
Implementing secure IAM permissions is just one part of running an effective security program in Amazon Web Services. Dash continuous compliance monitoring enables organizations to automatically detect and resolve security concerns in IAM and other AWS services. Organizations must implement solutions such as backup, disaster recovery, audit logging, and intrusion detection in order to establish a robust cloud security plan. Learn how Dash enables organizations to build strong security and compliance programs.


