Administrative security policies are a core part of any effective security and compliance program. In fact, security auditors as well as most clients, expect teams to have established policies as part of their overall security program. Regulatory frameworks and compliance standards including SOC 2, HIPAA/HITECH, and ISO 27001 require organizations to have internal policies in place in order to satisfy the administrative requirements and safeguards that these frameworks demand.
Not sure how to get started with security policies? Below we will outline best practices for building security policies and administrative controls.
Creating Security Policies
Goals Of Effective Policies
An administrative policy is a document that outlines standard operating procedures (SOPs) and general practices within the organization.
When we talk about “administrative policies” or “security policies” in this guide our aim is not just to create a paper document, but to connect and enforce these policies to technical controls and meet security and compliance objectives.
The overall goal of developing administrative policies is to create a general security framework that your team can implement across your organization and IT infrastructure. Created policies provide a step-by-step guide your team can follow to maintain security standards. Additionally, policy documents can be shared with clients, investors, and auditors.
Writing Realistic Policies
One of the most important considerations when developing security policies is to ensure that they set realistic and achievable security objectives within the organization. While it may be tempting to implement the most rigorous security standards, your team should define policy standards that are realistic rather than aspirational.
Writing policies that are unrealistic or not properly followed will undermine your team’s security program and will lead to issues during security procurement or future security questionnaires.
For example – If your team consisted of only 5 staff members, performing an internal penetration test quarterly would be an unrealistic expectation for your team. In this case, it makes more sense for the security team to perform this type of testing on a less frequent basis.
Reviewing and Revising Policies
Policies are only effective if they are kept up-to-date and are followed to the letter. Teams should occasionally review and update policies and procedures to reflect changes and growth within the organization.
When your policies change, your security controls should change to address these new standards as well. You should consult with your DevOps team to ensure that security configuration is updated alongside these updated policy standards. Learn how Dash ComplyOps can help your team implement and enforce administrative policies.
What To Include In Security Policies
Policies should be designed around your team’s organization structure, technologies, and security and compliance needs. Teams may take into consideration team sizes, available resources, and regulatory and security standards, such as SOC 2, ISO 27001, and HIPAA/HITECH, GDPR standards that need to be addressed.
For most security programs, security teams should consider developing security policies that address the following standards.
Managing Staff and Roles
A key component of security policies is defining security roles within your organization. These security roles outline individual responsibilities and address security implementation and management of policy standards listed below. Teams should consider assigning the following roles and responsibilities to staff within the organization:
- Security Officer & Privacy Officer
- DevOps/SecOps teams
- Incident Response teams
- Other necessary roles such as GDPR data protection officer (DPO)
Data Protection and Data Security
To ensure compliance, teams must also set data protection standards. This means companies should address data security standards such as encryption, access control, and audit logging. Security policies should address these technical security standards including:
- Data encryption at-rest and in-flight
- Role-based access control
- Multi-factor Authentication (MFA)
- Network security and limited port access
- Vulnerability scanning of code/services
- Audit logging and event collection
These controls involve technical configuration by the DevOps and SecOps teams.
Availability, Disaster Recovery, and Incident Response
Teams must also address overall service availability and plan for potential security and availability incidents. Clients, partners, and security auditors want to ensure that data is secured in a safe manner and that teams can respond to unforeseen scenarios. Security policies should be developed and document procedures for:
- Status and availability monitoring for servers/clusters
- Backup and disaster recovery (DR) services
- Contingency plans in case of an outage or security event
- Breach and notification processes
Privacy, Confidentiality, and 3rd Parties
Teams should address how they evaluate vendors, address confidentiality with employees, partners and vendors. Additionally, teams should also address all necessary privacy standards in the privacy policy provided to end users.
Building A Policy Aware Security Program
Having written documents is one thing, but how do security teams ensure that these policies are actually followed? Organizations should consider automated policy enforcement and developing towards continuous compliance monitoring.
Leverage Cloud Security Services
Teams using public cloud platforms such as Amazon Web Services (AWS) should leverage some of the many cloud services provided to meet security objectives.
Cloud platforms offer a lot of flexibility and configuration options when provisioning infrastructure, for this reason, it is important to ensure that new infrastructure is properly configured and meets security policy standards. Teams using AWS should consider overall service configuration and may consider using infrastructure-as-code (IaC) processes to manage security settings including the following:
- IAM to set users, roles, and permissions.
- Security Groups and NACLs to manage networking for instances and other resources.
- CloudTrail and CloudWatch to setup audit logging and collection of security events.
- Amazon GuardDuty to conduct vulnerability scanning across networks.
Automate DevOps and SecOps Processes
Cloud services like the ones listed above provide the ability for teams to build security processes, but ultimately it is up to your team to properly configure and manage these security standards across your environment. DevOps staff should work to develop configuration management processes, and ensure a consistent security baseline.
As your team grows you will need to provision new servers and containers, configure roles and permissions for new users and address other security standards. It is important that your team configures new infrastructure in a manner that meets your established security standards. Implementing a continuous compliance monitoring system, can help your team to set security controls and enforce a set security configuration, and maintain policy standards across your IT environment.
Manage Findings, Evidence and Reports
Teams should collect all security evidence necessary to prove that security controls and safeguards are in place. This means that your team should have documentation and reports on security controls, cloud security settings, and technical implementation.
- Review and resolve cloud security findings – Teams should assess cloud security standards across their infrastructure, identify problematic resources with configuration issues, and resolve any outstanding issues.
- Keep an inventory of cloud security controls – Teams should keep an inventory and collect evidence related to data security and configuration of cloud services. Teams can use this evidence to prove that proper security standards are implemented.
- Collect relevant documentation – Teams should gather all relevant security documentation provided by cloud providers and vendors. You may consider pulling together relevant service level agreements (SLAs), business associates agreements (BAAs), and security attestations.
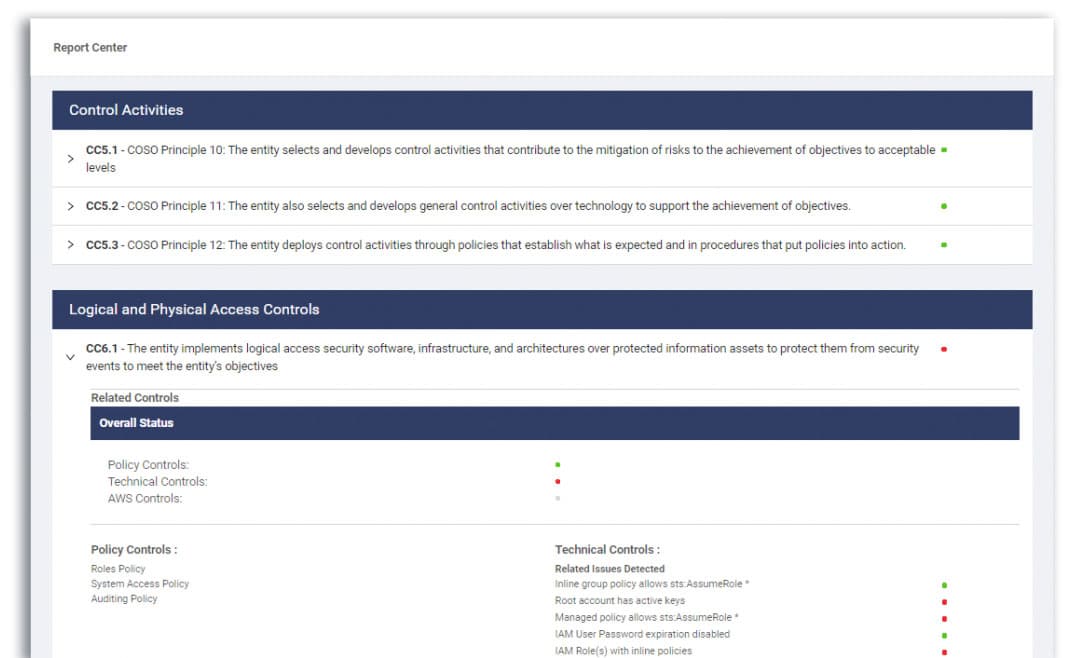
Dash ComplyOps can help your team to monitor and collect security evidence to prove that your organization is maintaining standards.
Working With Auditors
In order to pass client security risk assessments (SRAs) and security audits and attestations, teams need to be prepared and have an established security program within their organization.
Having an up-to-date set of policies helps to streamline the overall security process and audit process. By having the appropriate policies in place, your team will be able to provide information around security standards and protections your team has in place and more easily answer risk assessments and security questionnaires.
Teams should utilize policy documents alongside evidence and reports mentioned in the above section to address security assessments.
Conclusion
Having up-to-date administrative policies or “security policies” within your organization is the cornerstone to maintaining a robust compliance program. Administrative policies provide the outline and objectives for maintaining security standards within the organization.
By creating effective policies and automating standards through strong DevOps processes, your security team can maintain a robust security program with less overhead. Learn how Dash ComplyOps can help your team to create security policies and to enforce them through cloud security controls.
If you have further questions about security program development feel free to reach out to the Dash team.


