Building a Security Program in AWS
Cloud security and governance is becoming increasingly important as more organizations move data and applications to the public cloud. It is essential that organizations establish cloud security programs that fit organizational, staff and technology needs.
While AWS provides many cloud services that address cloud security requirements teams need to manage cloud configuration security standards around:
- Access Control
- Encryption
- Audit Logging
- Firewall/Networking
- Backup and Disaster Recovery
- Intrusion Detection
- Vulnerability Scanning
While creating policies and security controls are essential for teams building for security and compliance in the cloud, it is often difficult to determine whether these policies and controls are correctly implemented and in-place as cloud resources are added and changed. Organizations should look at creating a continuous compliance monitoring process to monitor cloud configuration. Using services such as Dash ComplyOps and AWS Config enables your team to ensure that security standards are up-to-date and have not been affected by organizational drift.
Managing Compliance Standards in The Cloud
Companies operating in regulated industries such as healthcare and finance and organizations selling to enterprises often need to meet regulatory requirements and achieve compliance with cybersecurity frameworks (CSFs) including HIPAA, PCI DSS, HITRUST, and SOC 2.
In order to meet security and compliance requirements in the AWS and the cloud, teams must handle security responsibilities. Most cloud service providers including Amazon Web Services (AWS) operate on a shared responsibility model. Under this model, security requirements are shared between the cloud provider and the cloud customer. While AWS will provide a signed business associates’ agreement (BAA) and physical security standards such as locked servers and limited employee access, organizations are responsible for setting cloud security controls/settings and creating all administrative policies and procedures.
Security and AWS Config
AWS Config provides cloud customers with the ability to set security “rules” and guidelines for AWS account security and governance. Rules are based around security best practices for individual cloud services and are defined by your security team. AWS Config then checks your AWS environment and reports violations to set security rules.
For example, AWS Config provides security rules that can be configured to:
- Flag EBS volumes that are unencrypted
- Flag RDS clusters that are running across multiple availability zones (AZs).
- Flag AWS resources that do not contain expected “tags”.
Security teams can view these cloud configuration findings for their AWS account and work to resolve these security issues to meet cloud security standards.
AWS Config Best Practices
AWS Config provides many options for customizing security controls. Teams should implement security rules that are relevant to their organization, development stack and address security program requirements.
Teams should follow best practices for AWS Config Rules:
Create AWS Config rules around your security policies and procedures: Teams should build administrative policies and procedures around your organization. AWS Config rules should be implemented to address standards set in these policies.
Set roles for responding to and resolving AWS Config issues: Teams should define which staff members and DevOps team members are responsible for viewing, addressing and responding to security issues.
Build workflow around AWS Config security findings: Teams should have a workflow in place for managing issues and ensuring that changes to cloud resources do not break applications and cloud services. Dash ComplyOps can help teams track and manage cloud security issues.
Evaluate AWS Config rules and configuration on a periodic basis: Teams should review AWS Config rules frequently and ensure that rulesets are up-to-date to reflect security policies and technology needs.
Setting Up AWS Config Rules
Your team can start evaluating cloud infrastructure and security configuration by enabling AWS Config, defining resources, and creating rules. AWS Config pricing is based on the number of Config rules, number of configuration items recorded, and the number of conformance pack evaluations.
In order to start utilizing AWS Config, your team should take the following steps:
- An AWS user with AWS Config permissions should login to the AWS Console and navigate to “Config” in the cloud services.
- Click “Get Started Now”.
- On the Settings page, for Resource types to record, specify the AWS resource types you want AWS Config to record.
- Setup AWS Config settings.
- Setup an Amazon S3 Bucket, to send configuration history and snapshot files.
- Select an SNS topic for streaming notifications.
- Define a IAM role for AWS Config permissions.
- View find Security Rule findings in the AWS Config Dashboard. You can click on individual non-compliant rules to view individual security issues.
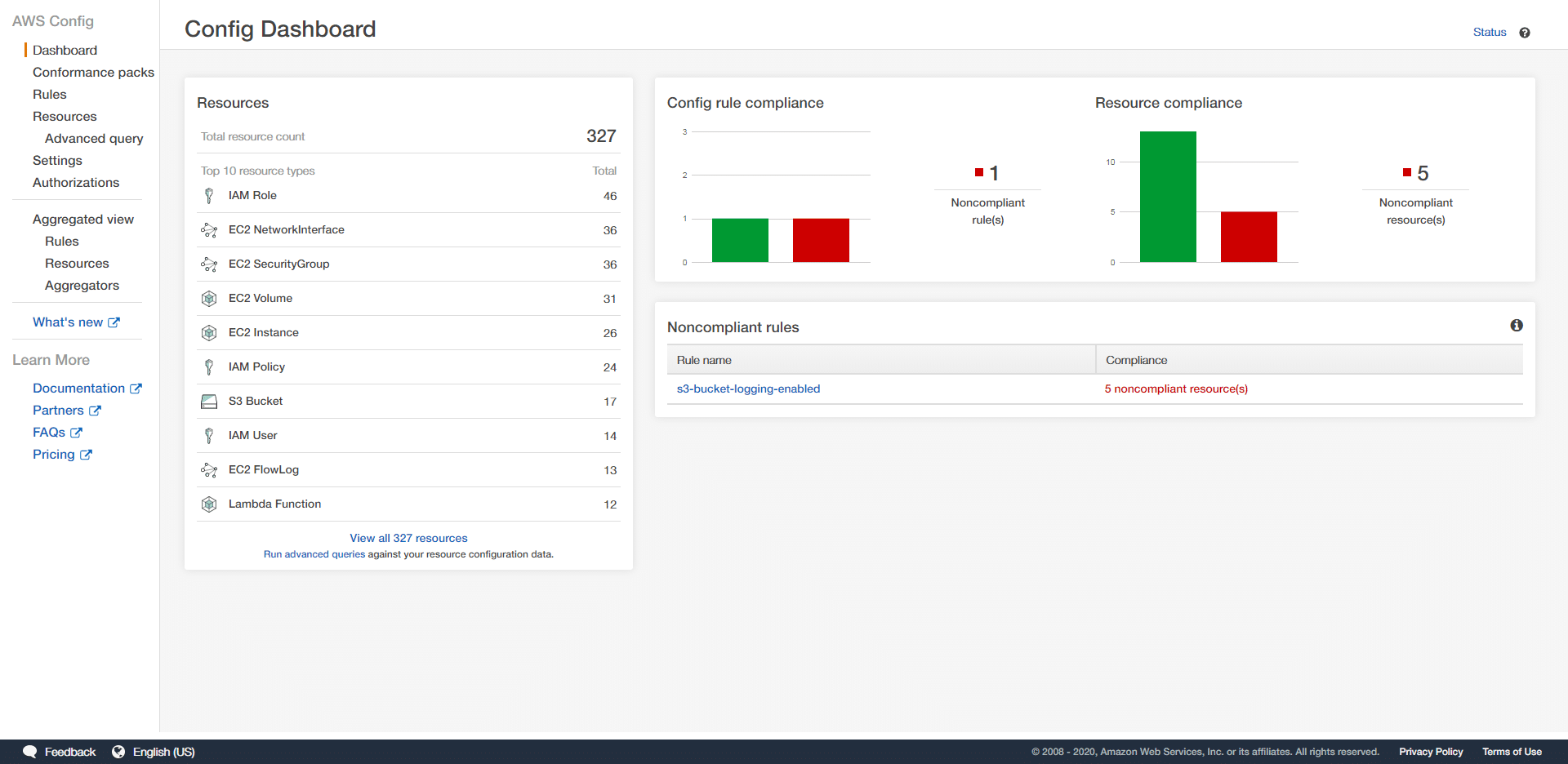
Connecting AWS Config into Dash
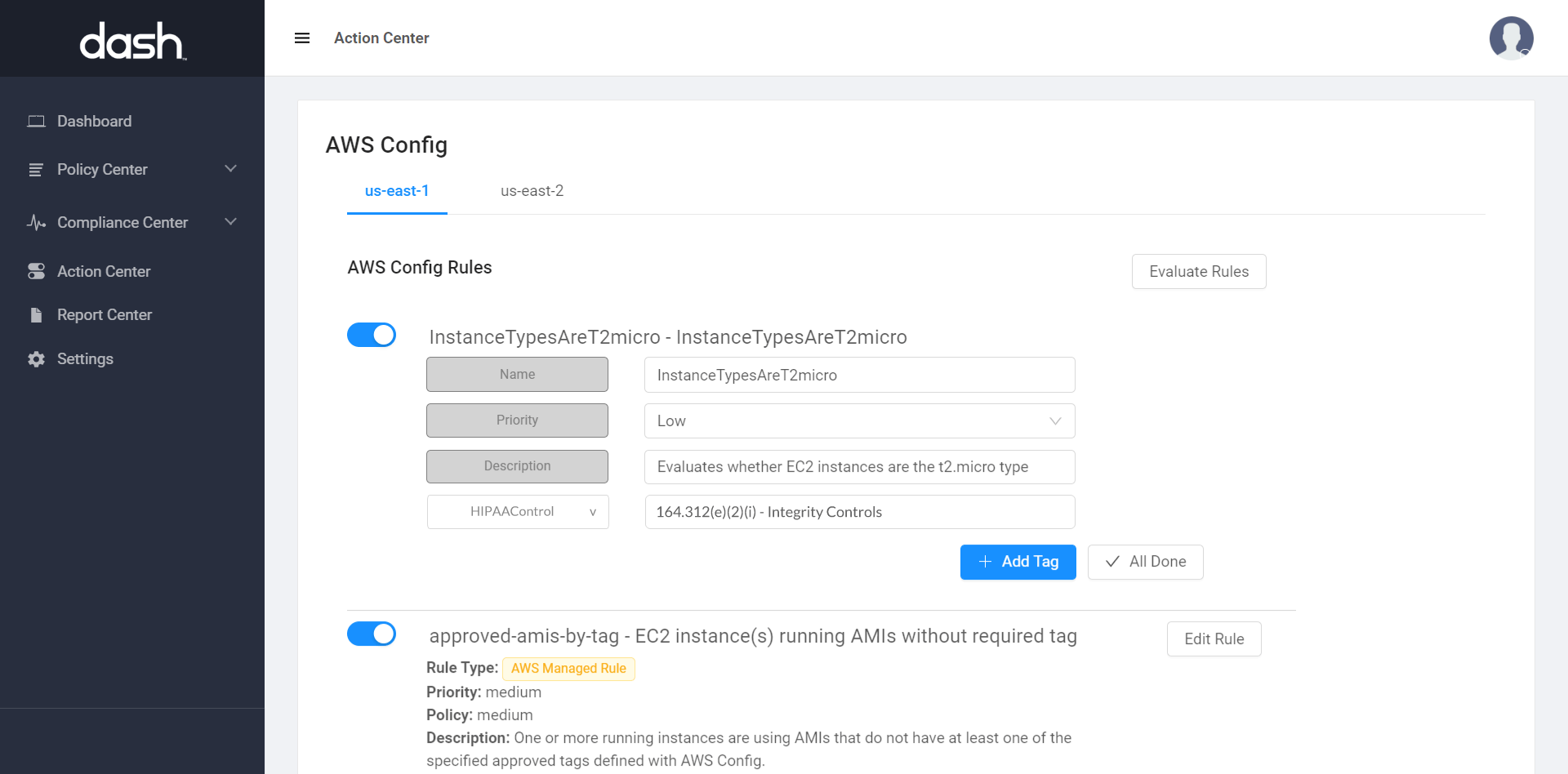
Setting up AWS Config Security Rules are a great way to start monitoring cloud security issues and enforcing cloud security controls, unfortunately it is up to your team to determine Rule settings and configure how findings fit into regulatory and compliance standards.
- Issue Assignment/Management
- Workflow
- Compliance Mapping
- Automatic Remediation
Dash ComplyOps provides teams with a compliance nerve center for managing compliance standards such as HIPAA, HITRUST, and SOC 2 in AWS. Teams can create formal administrative policies, and address cloud security issues detected by Dash monitoring and AWS native services including AWS Config. Dash connects cloud security scans to compliance mappings and provides additional information for remediating security concerns in your environment.
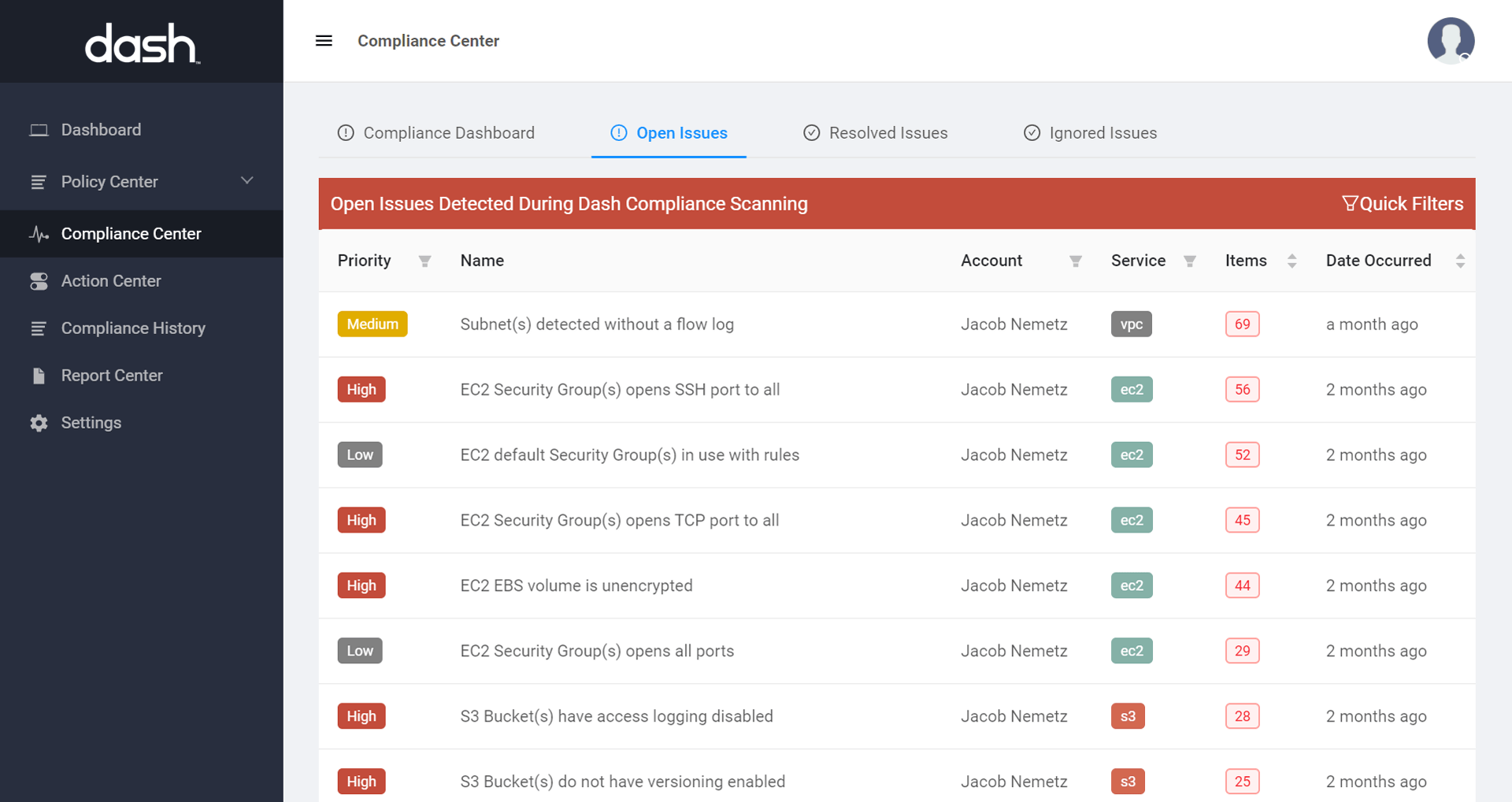
Security teams can customize Config scan metadata and compliance mappings to utilize AWS Config rules within their security and compliance programs.
Additionally, security teams can create reports and inventory security controls from Dash and services such as AWS Config, in order to validate security program and prepare for audits and security risk assessments (SRAs). This means that teams can see the compliance state of their environment in real-time. Create a report around regulatory standards and compliance frameworks such as HIPAA/HITECH, and SOC 2.
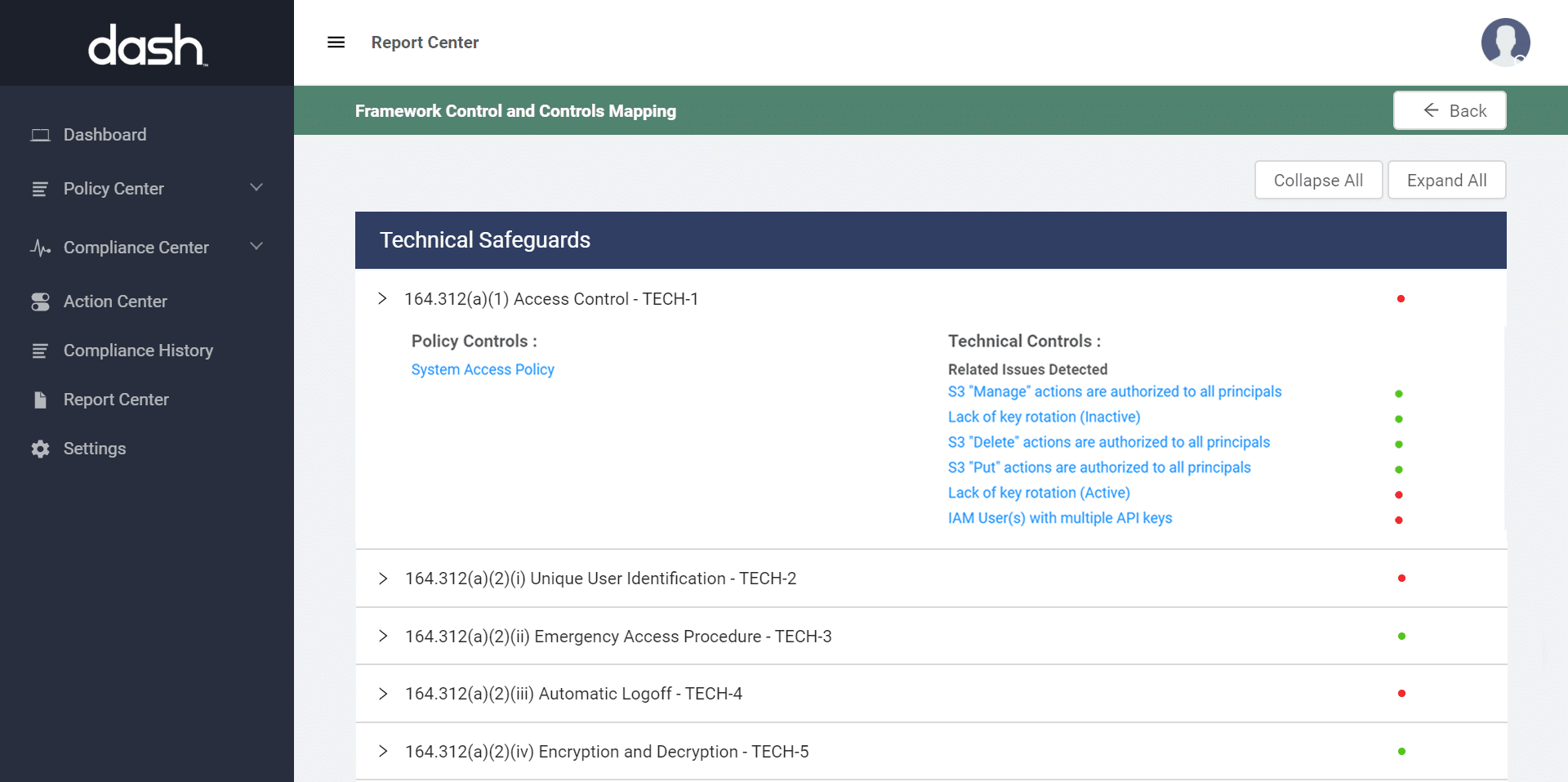
Enforcing Continuous Compliance Monitoring
Traditional security audits only provide a single point-in-time assessment for an organization and their infrastructure. It is hard for security teams to determine how well cloud security standards are followed and enforced within a year or even one week.
This is where building a continuous compliance monitoring system around solutions such as AWS Config and Dash ComplyOps can provide better visibility into your cloud security and cloud configuration. Your team can utilize these tools to better manage your cloud security posture and maintain a robust security program in Amazon Web Services (AWS). With Dash you can build a custom security program around your team’s needs, set security controls, and automatically remediate issues. Learn how Dash can help your team automate AWS cloud security and compliance.


