SOC 2 (System and Organization Controls 2) is an auditing framework that service providers go through in order to ensure proper data and privacy protections regarding sensitive data are in place.
SOC 2 is designed to test and provide a report surrounding an organization’s internal security controls. Once obtained, a SOC 2 report can be provided to potential clients, partners, and other third parties, as proof of a robust security program. Large enterprises often require security certification or validation from potential vendors in order to evaluate vendor risk. Many startups, software companies, and SaaS businesses that work with data in regulated industries heavily rely on SOC 2 reports as documented proof that their security measures are up to date.
Why Should Startups Care About SOC 2?
Obtaining a SOC 2 report is an effective way to demonstrate the security posture of your startup organization and impress potential clients. SOC 2 reports are considered a comprehensive measure of an organization’s security profile, as such, SOC 2 certification can benefit a startup in many ways, including:
Establishes Credibility with Clients and Investors
Vendor security is a serious concern for established companies and large enterprises. According to a recent report, 83% of organizations experienced a third-party security incident in the past three years (Deloitte). With growing security concerns, organizations are now more carefully vetting new software solutions and software vendors.
Successfully completing a SOC 2 audit is a fantastic way to prove the effectiveness of your security controls and ease security concerns to Fortune 500s, regulated industries such as financial services and healthcare, and potential investors. After completing a SOC 2 audit, you’ll be fully prepared to handle any security and compliance-related questions from clients and security risk assessments (SRAs).
Provides a Competitive Advantage
Since security breaches are a very real concern for companies both large and small, having the willingness to undergo a SOC 2 audit demonstrates an organization’s dedication to a strong security posture. Having a current report shows that your company has all necessary controls to secure confidential data and personally identifiable information (PII). In turn, such commitment allows your company to stand out from the competition and build early trust in the marketplace.
Assists in the Development of Strong Policies and Procedures
Thanks to the rigorous testing and standards involved in the SOC 2 auditing process, upon completion, your organization will emerge equipped with formally defined policies and procedures. These policies define key processes and controls throughout your organization and business operations. Aside from mitigating potential security risks formally defined policies and procedures provide a foundation for your company’s security program. Your team can build on this security program in the future.
SOC 2 is Easier to Achieve in the Startup Stage
The desire to put off a SOC 2 audit in the infancy of a company is understandable. Often, startups have limited access to resources and are typically hyper-focused on product development and innovative patient outcomes rather than security and regulation. Unfortunately. putting off the inevitable will only make things more complicated in the future.
Consider the following: during a SOC 2 audit, evidence needs to be gathered by various departments and personnel across an organization — this is much easier to pull off while your team is still small, where auditing requests can be addressed quickly, in an organized fashion. Furthermore, ensuring that internal controls meet SOC 2 standards early on will only strengthen and enhance your team’s security knowledge, allowing you to be better prepared for future compliance audits.
SOC 2 Lowers Your Risk Profile
According to IBM, the average cost of a data breach for an organization is $3.62 million. Furthermore, a staggering 44% of enterprises have reported having experienced a data breach caused by a vendor (HelpNetSecurity). Large enterprises must ensure that any potential new vendors and/or software solutions have up-to-date security measures in place that will not jeopardize their organization. If your organization doesn’t have a SOC 2 report, then large clients may find another vendor that does — your solution may be considered a security risk. Having a current SOC 2 report helps alleviate client security concerns and lowers your company’s overall risk profile.
Types Of SOC 2 Reports
There are two types of SOC 2 reports organizations can be evaluated for – SOC 2 Type 1 and SOC 2 Type 2. Companies should consider the differences between reports and determine overall report and certification objectives when preparing for an audit.
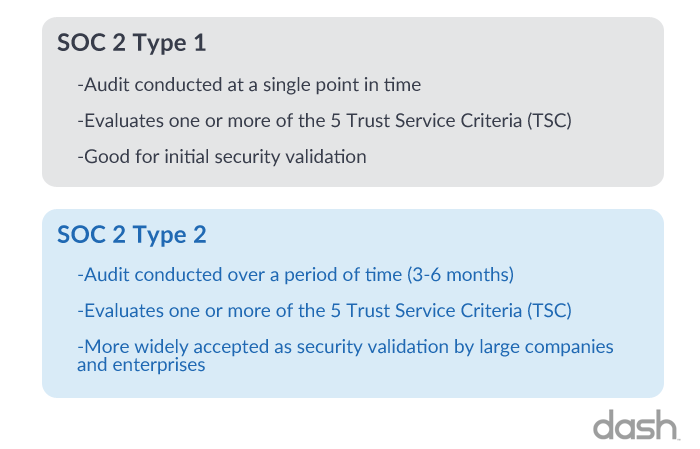
A SOC 2 Type 1 report evaluates an organization’s system and implementation of security controls related to the Trust Services Criteria (TSC) at a single point in time.
A SOC 2 Type 2 report evaluates an organization on the same set of security controls and Criteria as a Type 1 report, but also evaluates an organization on it’s operating effectiveness of controls over time.
What Type of SOC 2 Report Do Startups And Software Companies Need?
Startups and software companies may consider receiving a Type 1 report as initial validation for clients and proof that the company is serious about developing it’s security program. A Type 1 report generally has a lower cost to achieve and can show that a company is tracking towards a more robust security program.
With that said, a Type 1 report is quite limited. Since the audit is conducted at a single point in time, it can quickly become outdated and the report becomes less meaningful as time passes.
A Type 2 report is the gold standard for SOC 2 security assessments and validation. Since SOC 2 Type 2 evaluates an organization’s security controls for a 6 month period or longer, it provides greater security validation for the organization. A Type 2 report is often more useful for demonstrating your company’s security posture and passing through client procurement.
Ultimately it is up to your team to determine what SOC 2 report is right for your organization and what is being required by your clients and partners.
SOC 2 Compliance For Startups In 4 Steps
In order to prepare for and achieve SOC 2 certification, teams must establish security controls, consult with a reputable auditing firm, and validate the effectiveness of their security standards through a security audit.
To achieve SOC 2 certification quickly and effectively, an organization must be properly prepared before the formal auditing process begins. The auditing process can be expedited by gathering and providing the appropriate SOC 2 evidence, including administrative policies, and technical security standards.
Remember: A company that is prepared for security assessment will deal with less scrutiny and achieve certification quickly.
1. Ensure Administrative Security Policies Are Up-to-date
These policies are an essential component of any security program. Your policies should reflect your employee structure, technology, and everyday workflow. These are not legal documents — be sure they are simplified, written in plain English so they can be easily read and understood by all staff members.
Your security policies should simply outline how your security controls are implemented across your applications and infrastructure. Make sure to highlight and define all of the necessary steps for managing security.
Be sure to outline the standard security processes including the following topics:
System Access: How user access to sensitive data is both granted and revoked.
Disaster Recovery: How both backup and DR standards are implemented, tested, and managed.
Incident Response: How security incidents are reported, investigated and resolved.
Risk Assessment and Analysis: How your organization assesses, manages, and resolves security issues and security risks.
Security Roles: How security staff roles, and responsibilities are delegated within your organization.
Security Training: How security awareness training is implemented throughout your organization.
Once your administrative policies are up to date, be sure to review, assess and continually update them as your procedures gradually change. These policies can be presented to auditors as proof that your team has current security plans and safeguards in place.
2. Set Technical Security Controls
Auditors ensure compliance standards are met with one or more of the AICPA Trust Service Criteria (TSC). In order to achieve SOC 2 certification and receive a SOC 2 report, your team must ensure that all data security and privacy protections regarding sensitive data are in place.
Trust Services Criteria (TSC) consists of the five following categories of criteria. Security teams should implement the following related controls when preparing for these criteria including:
Security: network/application firewalls — two-factor authentication — intrusion detection
Privacy: access control — two-factor authentication — encryption
Confidentiality: confidentiality agreements — access controls — encryption
Processing Integrity: quality assurance — processing monitoring
Availability: performance monitoring — disaster recovery — security incident handling
Startups and software companies operating in the public cloud (AWS, Azure), should configure all necessary cloud security safeguards within their IT services to meet SOC 2 internal controls. Security teams may look into SOC 2 compliance automation to establish security settings including access control, encryption, network and firewalls, disaster recovery.
Note: Make sure that your security controls are implemented to meet the latest SOC 2 Trust Standards Criteria — Download a list of the latest security controls here.

3. Gather Security and SOC 2 Control Evidence
After setting administrative policies and implementing security controls to meet SOC 2 criteria, teams should collect all relevant security evidence to prepare for SOC 2 audit. Having this evidence ready, will enable your team to answer auditor inquiries and complete the audit process in less time.
Your security team may consider gathering documentation and and security evidence including the following to prepare for an upcoming audit:
- Cloud Security Information
- Access Control Settings
- Evidence of Encryption (at-rest and in-flight)
- Evidence of Backup Creation
- Evidence of Log Collection
- Evidence of Intrusion Detection Systems
- Evidence of Vulnerability Scanning and Patches Being Applied
- Cloud/Infrastructure Certifications and Agreements – Collect all cloud and infrastructure related agreements, certifications and attestations including documents such as:
- SOC 2 Report
- Business Associates’ Agreement (BAA)
- Service Level Agreements (SLAs)
- Administrative Security Policies – Collect and provide all administrative policies related to your security program.
- Technical Security Control Documentation – Collect any evidence and documentation around implementation and management of infrastructure security controls.
- 3rd Party and Vendor Contracts – Collect all documentation associated with third party companies, contractors, and service providers.
- Risk Assessment and Audit Documentation – Collect and provide any existing documentation from previous security assessments, or third-party audits.
Dash ComplyOps makes it easy for teams to prepare for, and achieve SOC 2 compliance. Dash works closely with startups and SaaS companies, to create custom administrative policies, establish cloud security controls, enforce SOC 2 internal controls, and gather SOC 2 evidence and artifacts through continuous compliance monitoring.
4. Perform a Formal SOC 2 Audit
Once all of the necessary SOC 2 security controls have been implemented and tested to meet the Trust Services Criteria (TSC), an organization is then ready to schedule a SOC 2 security audit. During the auditing process, teams will be asked to answer relevant security questions and provide policies and evidence relating to their security controls.
For evaluating security controls, assessors may ask for specific evidence around infrastructure and systems. As an example, an auditor may ask for evidence that servers/instances utilize encrypted volumes or that backups are enabled and being created for your production services.
Once your team is ready, you should consider looking for an audit firm/assessor with the following qualities:
Experience: Look for a firm that has considerable experience conducting SOC 2 audits. A firm that has performed numerous assessments on the latest SOC 2 criteria is highly recommended.
Project Fit: For best results, consider an auditing firm that has worked with similar types of organizations in the past. Auditors that have worked with other startups, SaaS companies, or companies within your industry will be better able to provide guidance to your team.
Excellent Communication: Only work with an auditing firm that has a reliable track record in communication, that responds to concerns and inquiries within a 24-hour period. A good communication loop allows teams to better address issues and progress through the assessment process with ease.
Maintaining SOC 2 Compliance
In order to receive a SOC 2 Type 2 Report, your organization must continue to prove the ongoing effectiveness of your security controls. For a Type 2 report, this means your company will be evaluated for a specific period of time, often 3 – 6 months. During this evaluation period, your company must continue to validate and provide evidence that security controls are still in place (IE. Your team is properly managing user access, creating backups, encrypting data etc).
It should also be noted that most SOC 2 reports only cover a 12-month period. This means an organization must complete a SOC 2 audit every year in order to maintain a current SOC 2 report.
Security teams may turn to Dash ComplyOps for streamlining the collection of security evidence, creating security policies, and ensuring SOC 2 internal controls remain in-place through continuous compliance monitoring.
Visit Dash to learn more about how security teams can streamline SOC 2 compliance and achieve SOC 2 certification quickly and painlessly.