SOC 2 Compliance Automation
Build and Maintain Your SOC 2 Compliance Program In The Public Cloud
What Is SOC 2?
SOC 2 is a reporting framework that defines security criteria for managing client data, and is developed by the American Institute of CPAs (AICPA). Enterprise companies, especially in regulated industries utilize SOC 2 reports as a measure of security preparedness and validation for SaaS solutions and outside vendors. Software companies should consider receiving a SOC 2 Type 1 or SOC 2 Type 2 report to build customer trust, obtain new clients, and streamline enterprise procurement.

How Do You Achieve SOC 2 In The Cloud
Prepare Security Program
Organizations should establish a SOC 2 security program that addresses Trust Services Criteria. Teams should develop administrative policies, implement cloud security controls, and gather all security evidence and documentation to prepare for an audit.
Perform A SOC 2 Audit
Organizations must engage with a AICPA-affiliated third-party audit firm to perform a SOC 2 audit. Teams should consider selecting a reputable firm that has worked with similar clients and security expertise.
Maintain SOC 2 Controls
After receiving a SOC 2 report organizations must continue to maintain SOC 2 internal controls across their AWS cloud environment. Teams must complete a SOC 2 audit every year in order to stay current with their SOC 2 report.


Develop Your Cloud SOC 2 Security Program
SOC 2 Security Criteria for The Public Cloud
Organizations operating in the public cloud are responsible for specific Trust Service Criteria and internal controls within their public cloud environment. Security teams are responsible for security controls including:
CC5.0: Control Activities – CC5.0 defines requirements for determining control activity types, implementing relevant infrastructure controls, and establishing policies and procedures for maintaining internal controls.
Teams operating in the cloud should create security policies that set standard operating procedures across the IT infrastructure and establish security controls, such as encryption, backup, access control, firewall, and intrusion detection standards across all cloud services. Dash ComplyOps tracks all administrative and technical control activities within your organization and cloud environment.
CC6.0: Logical and Physical Access Controls – CC6.0 defines requirements around managing access to data and systems.
Teams with public cloud infrastructure should define logical access controls using services such Identity Access Management (IAM) and VPCs, Security Groups and Firewall Rules, as well as setting encryption settings for individual cloud resources. Teams can enforce all logical access control requirements through Dash ComplyOps security monitoring.
CC7.0: System Operations – CC7.0 defines requirements for finding system vulnerabilities, responding to security incidents, and resolving security concerns.
Teams should implement cloud solutions vulnerability scanning, intrusion detection and audit logging and develop Vulnerability Scanning and Incident Response Policies. Teams may consider enabling audit logging with Cloudwatch and detecting suspicious network activity with GuardDuty. Dash ComplyOps can ensure that these security solutions are properly enabled across cloud resources.
CC8.0: Change Management – CC8.0 defines requirements for setting baseline system configuration and managing changes to software and systems.
Teams should create a set of baseline cloud security controls with a tool such as Dash ComplyOps and continue to monitor cloud resources for changes to security settings and overall configuration. Dash continuous compliance monitoring can automate this process.
Achieve SOC 2 Type II In The Public Cloud
Prepare For a SOC 2 Audit
Dash enables teams to plan and implement internal controls in the public cloud and achieve SOC 2
Set Security Policies and Cloud Security Criteria
Dash ComplyOps makes it simple for your team to identify SOC 2 security gaps across your cloud infrastructure and implement proper security controls.
Dash enables teams to create custom administrative policies mapped to the latest SOC 2 trust service criteria and enforce controls through continuous compliance monitoring.
Dash allows teams to:
- Define SOC 2 necessary administrative security policies
- Set cloud security controls for SOC 2
- Monitor and enforce security standards across your cloud environment
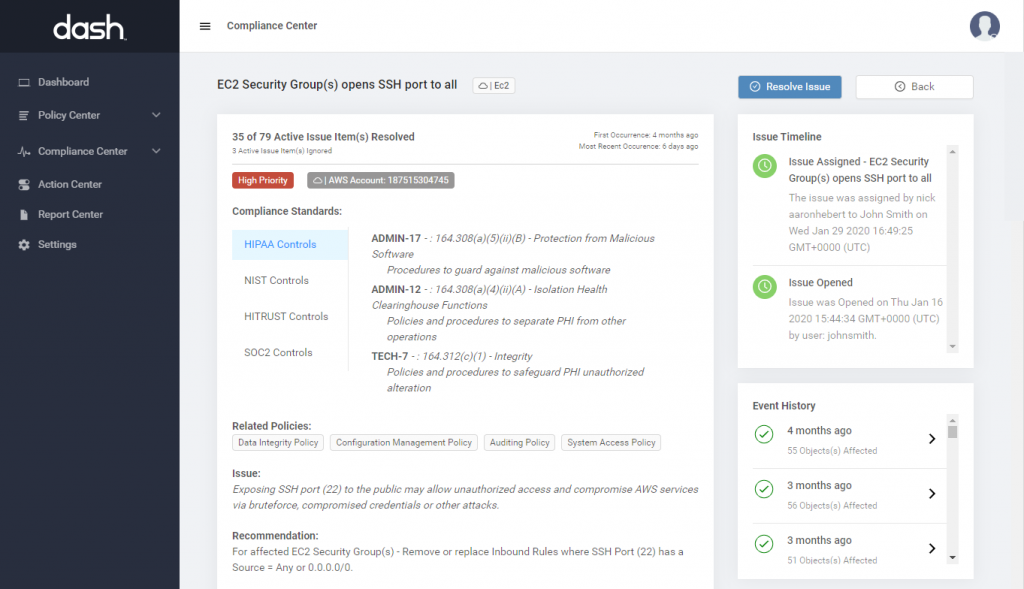
Inventory SOC 2 Cloud Security Controls
Teams should collect all relevant documents, security evidence and agreements. Teams should consider gathering the following security evidence for assessment:
- All current administrative policies
- AWS SOC 2 report and security attestations
- Agreements with vendors and third party contractors
- Evidence for all security mappings and implemented security controls
Dash automatically creates an inventory of SOC 2 security controls and collects all security evidence necessary for your SOC 2 audit.
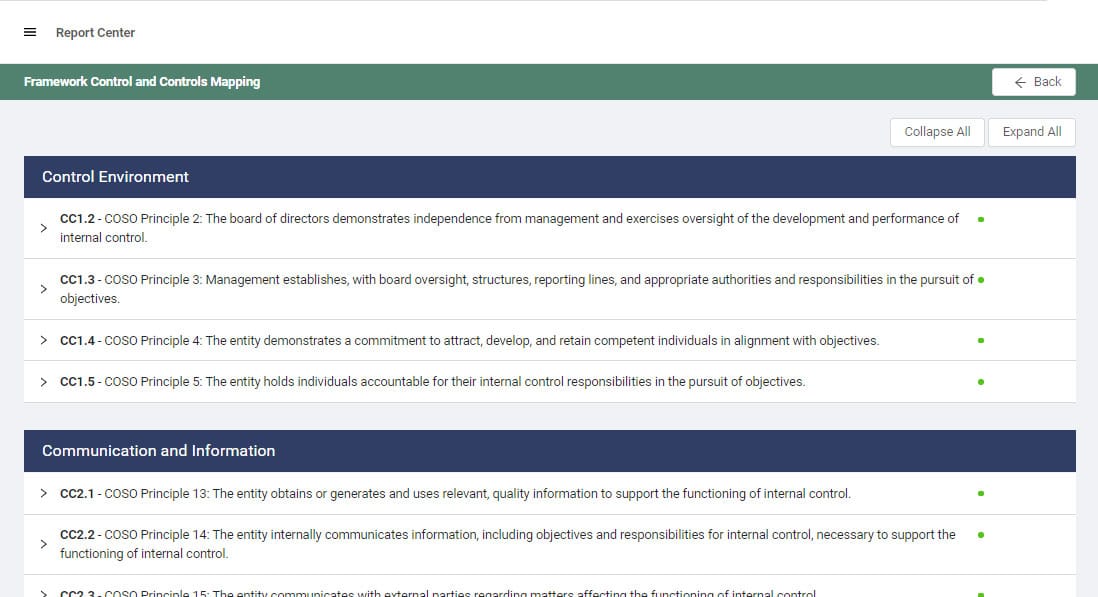
Achieve SOC 2 Compliance In The Cloud
Automate SOC 2 Controls and achieve SOC 2 Type 2