The Audit Process
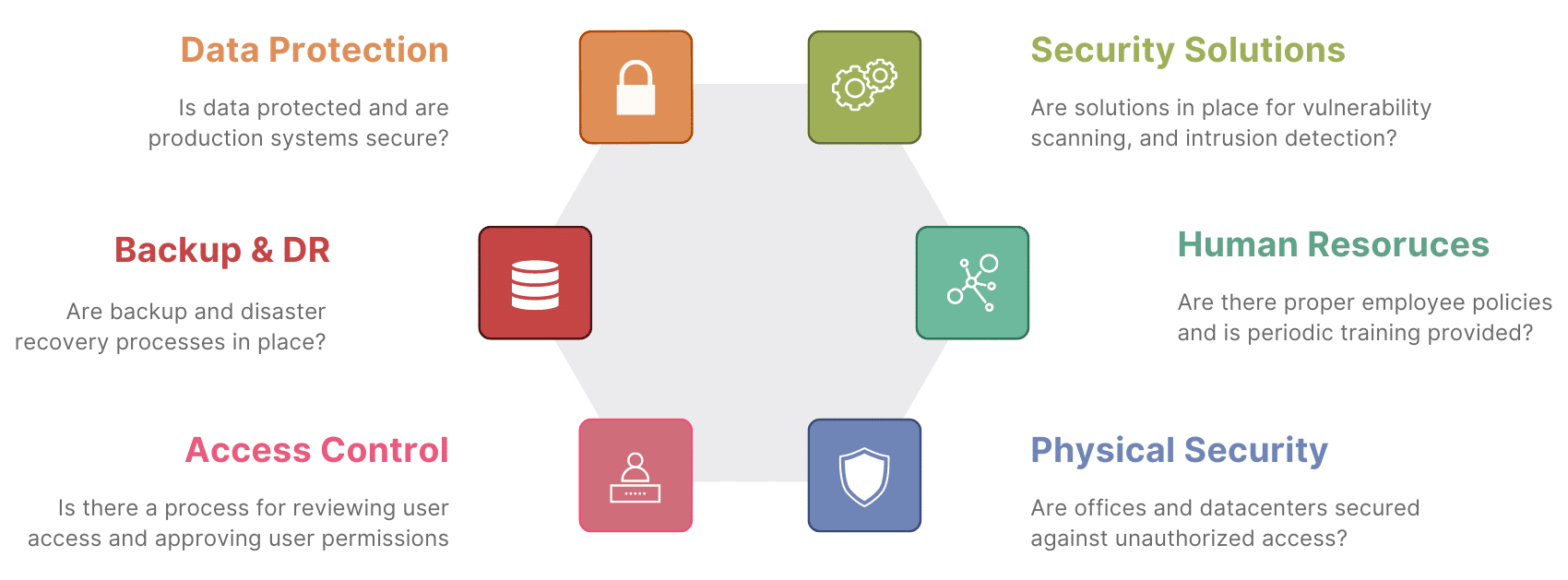
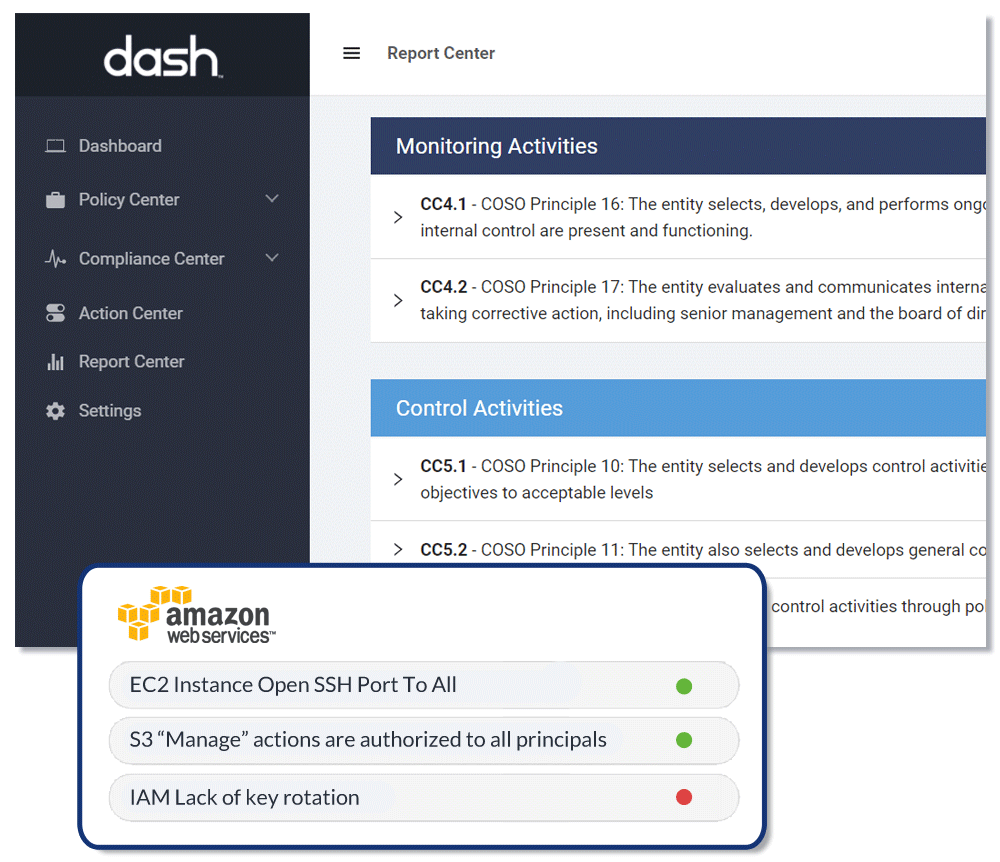
During a SOC 2 audit, an audit firm will typically request that organizations share further information on their security programs and evidence of security operations. The information needed by assessment firms may vary depending on the type of audit and Trust Service Criteria (TSC) your team is being assessed on.
Below are some of the categories and types of evidence SOC 2 auditors may request for evaluating your organization’s security program. To get a better idea of SOC 2 scope and requirements, companies should consider connecting with a firm to determine audit needs and overall scope.