Challenges of SOC 2 For Software Developers
Fro software developers creating solutions for enterprises and regulated industries, security is paramount. Achieving SOC 2 compliance enables software companies to validate security efforts and streamline security questionnaires and procurement when approaching potential clients, partners, and enterprises.
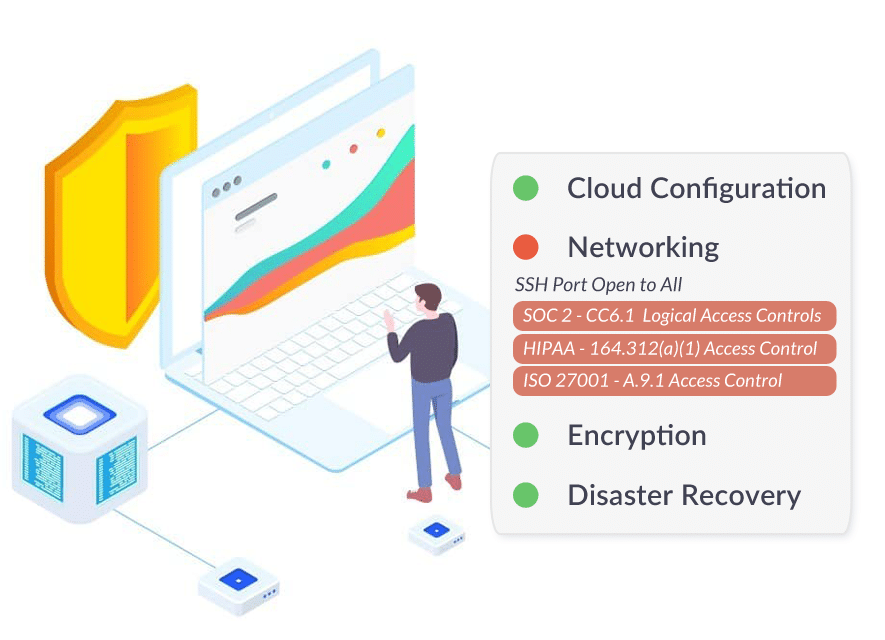
In order to receive achieve SOC 2 compliance, Software and DevOps teams must implement all applicable SOC 2 Trust Service Criteria (TSC) and complete an audit from a certified by a AICPA approved audit firm. Software development teams must adopt administrative policies and implement all necessary security controls for the cloud infrastructure. Software teams must address the following when building a SOC 2 compliance program:
- Finding A Reputable SOC 2 Auditor
- Determining Audit Scope and Assessment Criteria
- Implementing Applicable SOC 2 Trust Service Criteria (TSC)
- Maintaining SOC 2 Security Controls
- Gathering Security Evidence and Completing A SOC 2 Audit