Dash ComplyOps makes it easy for your team to build and manage your organization’s HIPAA security program.
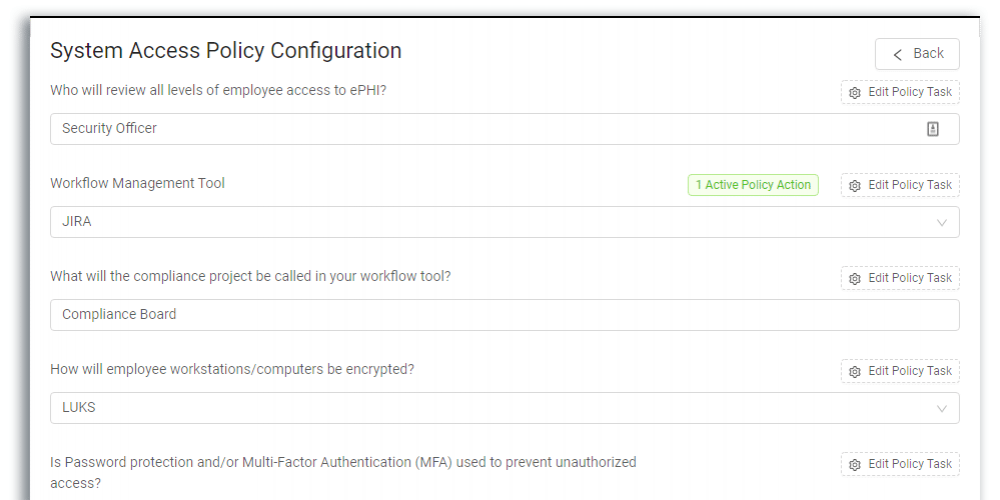
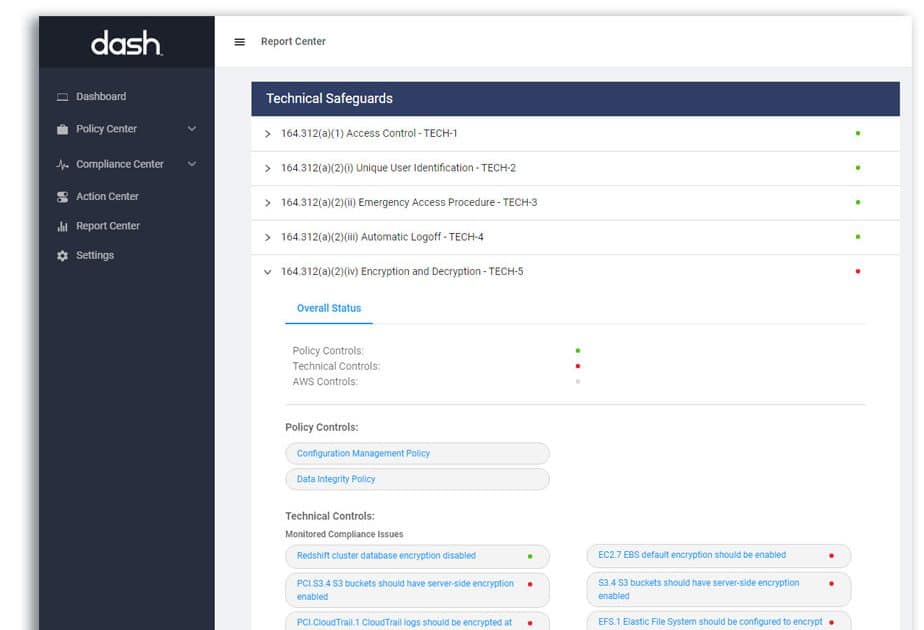
Dash enables teams to build custom administrative policies mapped to HIPAA requirements and enforce controls through continuous compliance monitoring.
Dash allows teams to:
- Define HIPAA Required Administrative Security Policies
- Set Security Roles Including Security/Privacy Officers
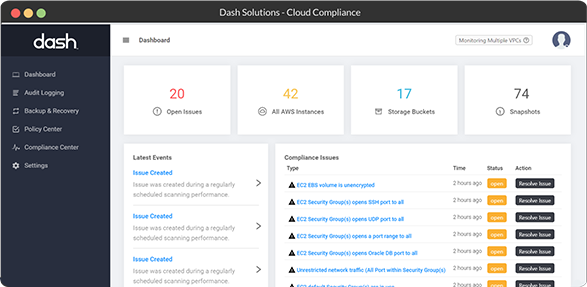
- Monitor and Enforce Policies Across Your Cloud Environment