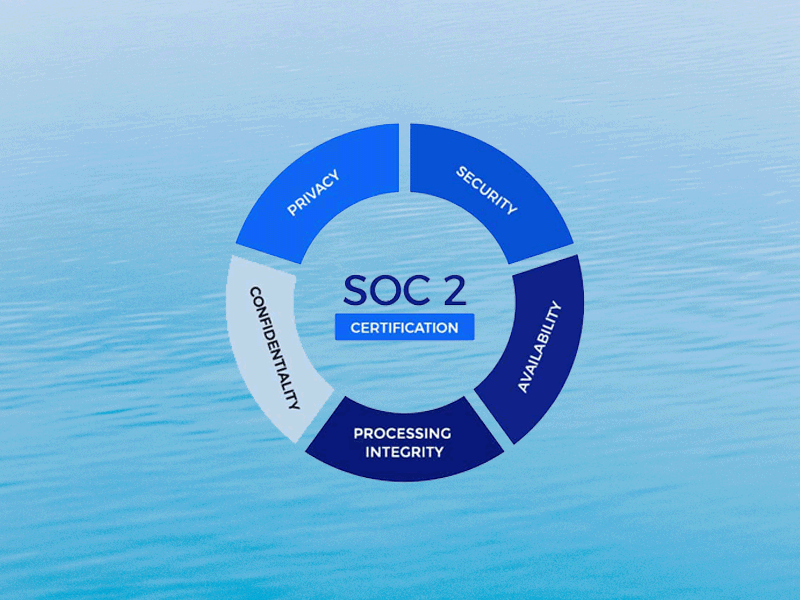
Organizations operating in the public cloud are responsible for specific Trust Service Criteria and internal controls within their public cloud environment. Security teams are responsible for security controls including:
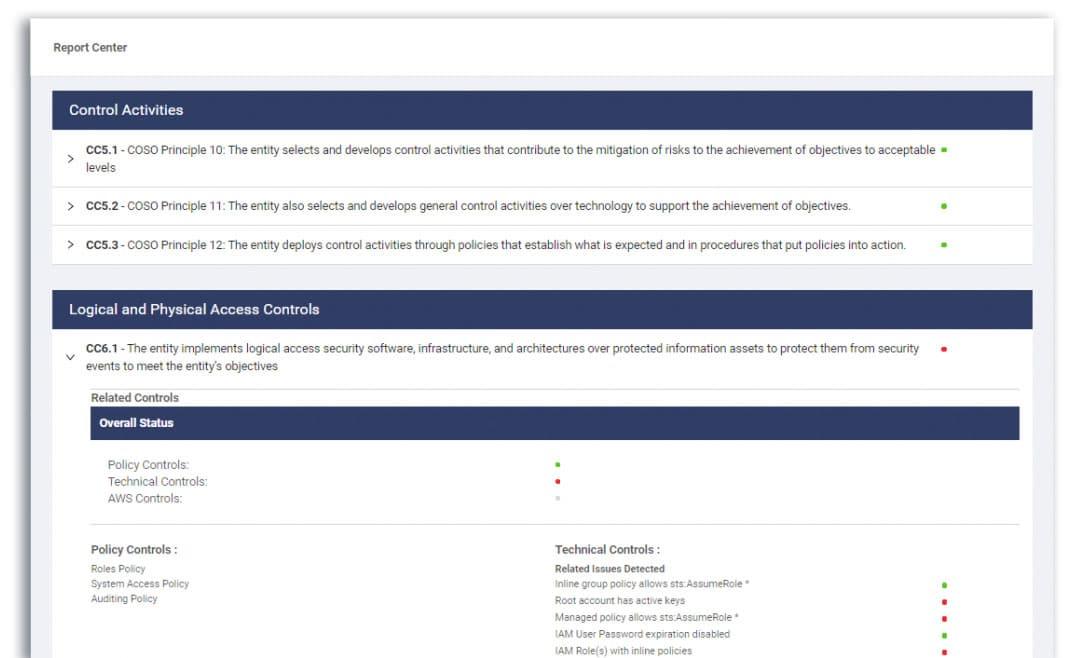
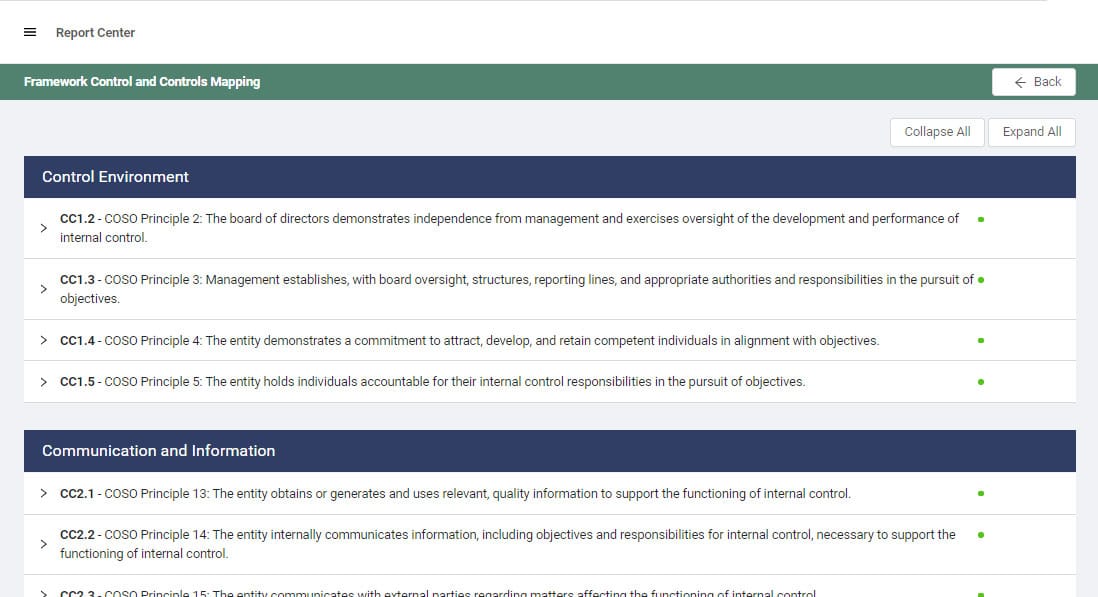
CC5.0: Control Activities – CC5.0 defines requirements for determining control activity types, implementing relevant infrastructure controls, and establishing policies and procedures for maintaining internal controls.
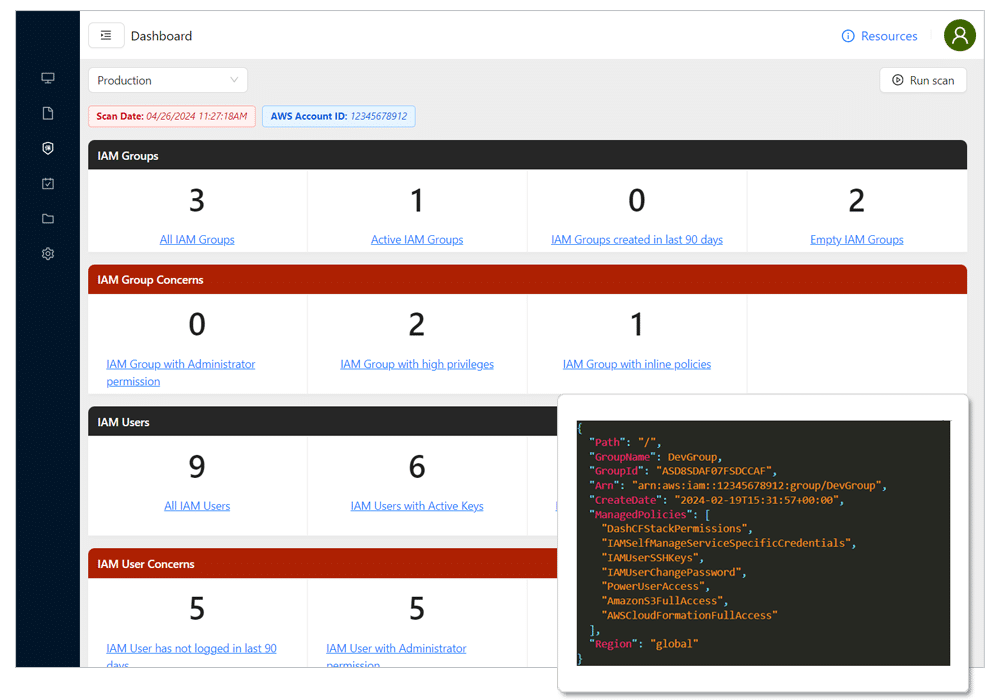
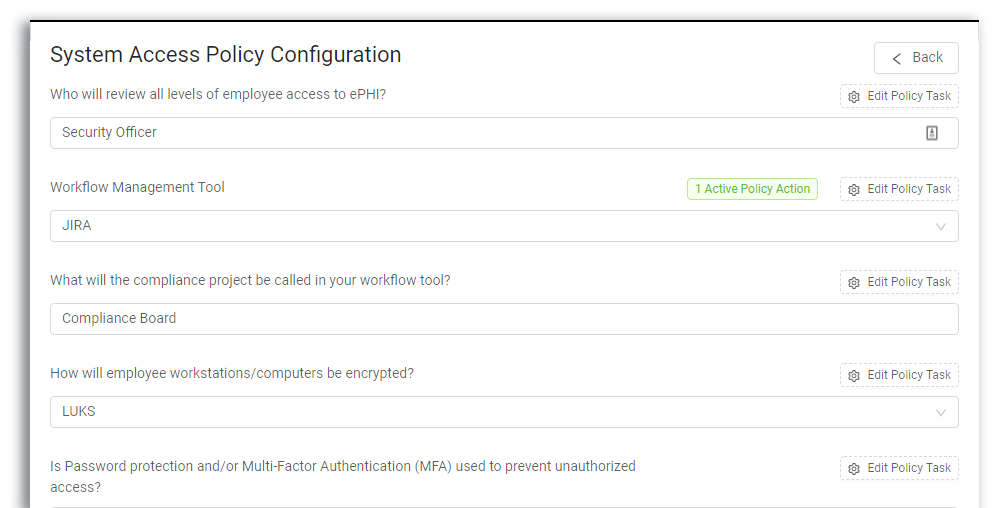
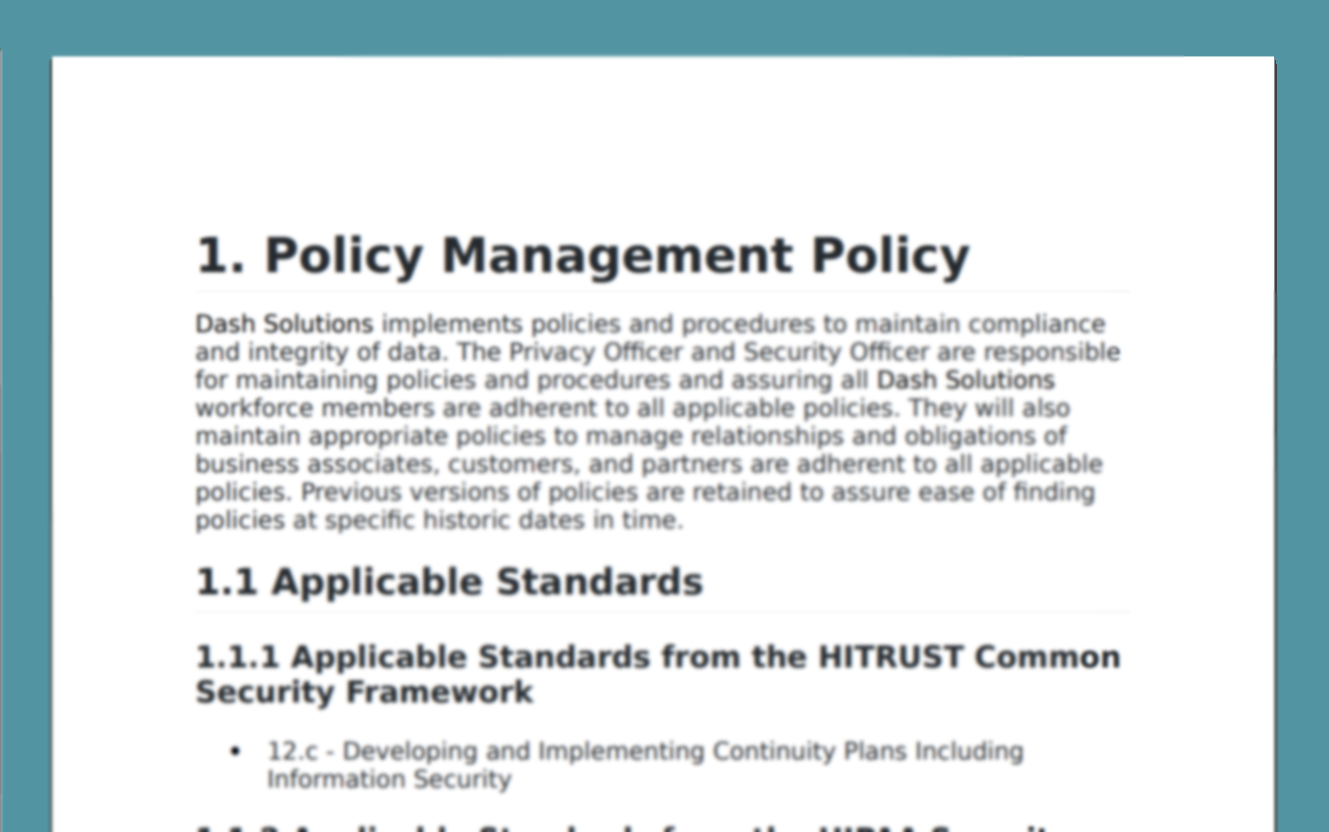
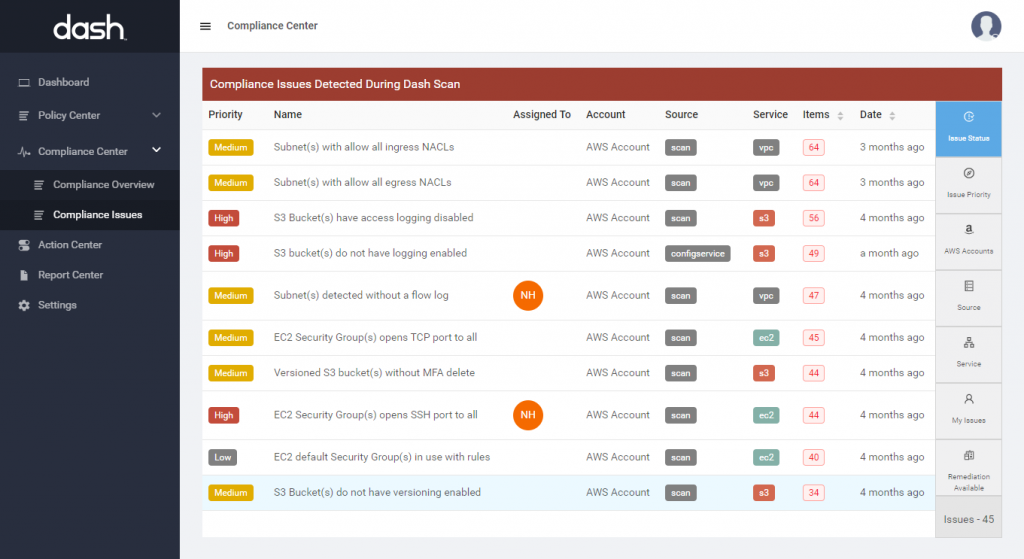
Teams operating in the cloud should create security policies that set standard operating procedures across the IT infrastructure and establish security controls, such as encryption, backup, access control, firewall, and intrusion detection standards across all cloud services. Dash ComplyOps tracks all administrative and technical control activities within your organization and cloud environment.
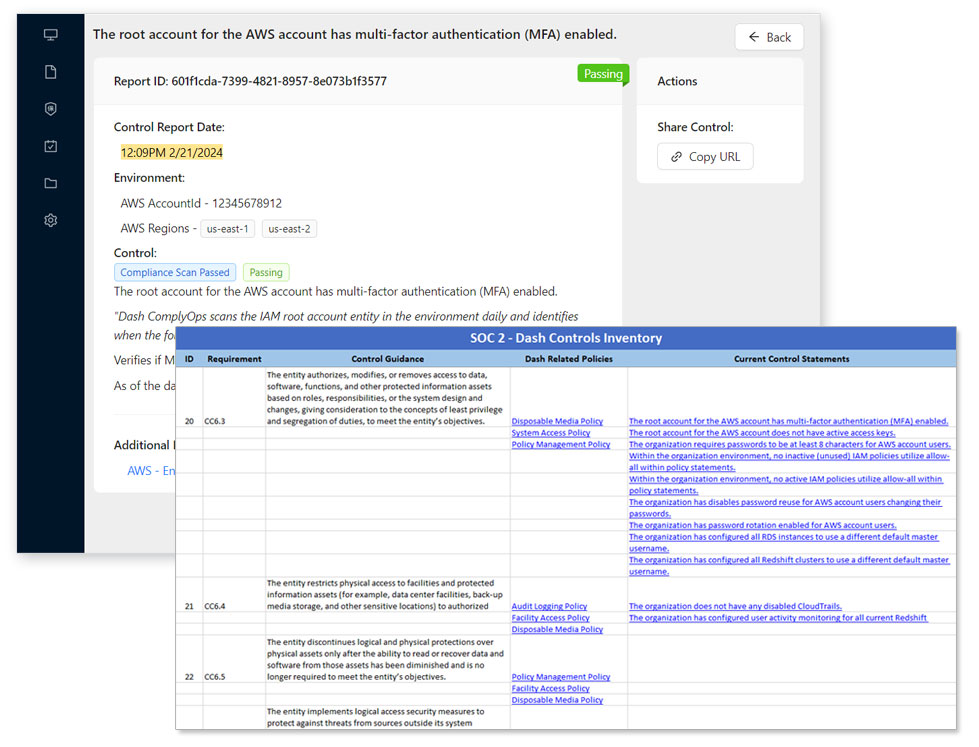
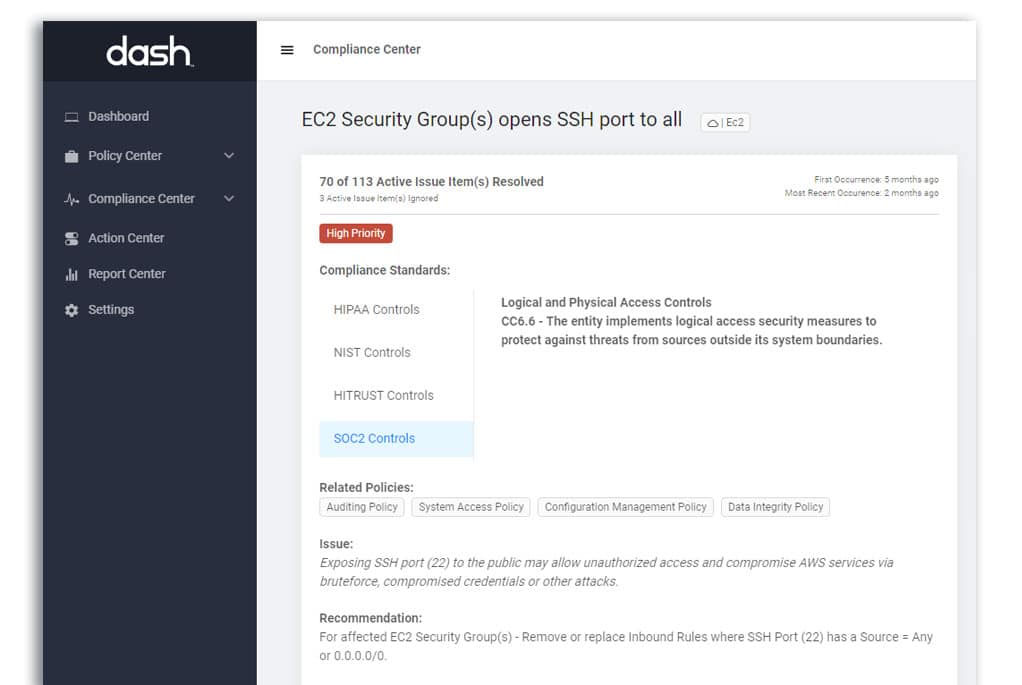
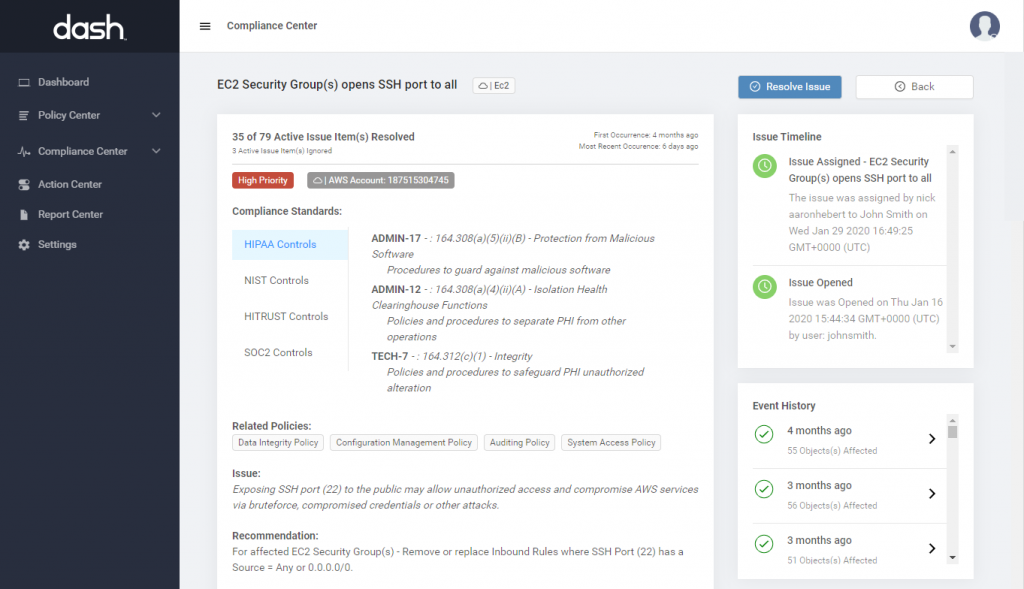
CC6.0: Logical and Physical Access Controls – CC6.0 defines requirements around managing access to data and systems.
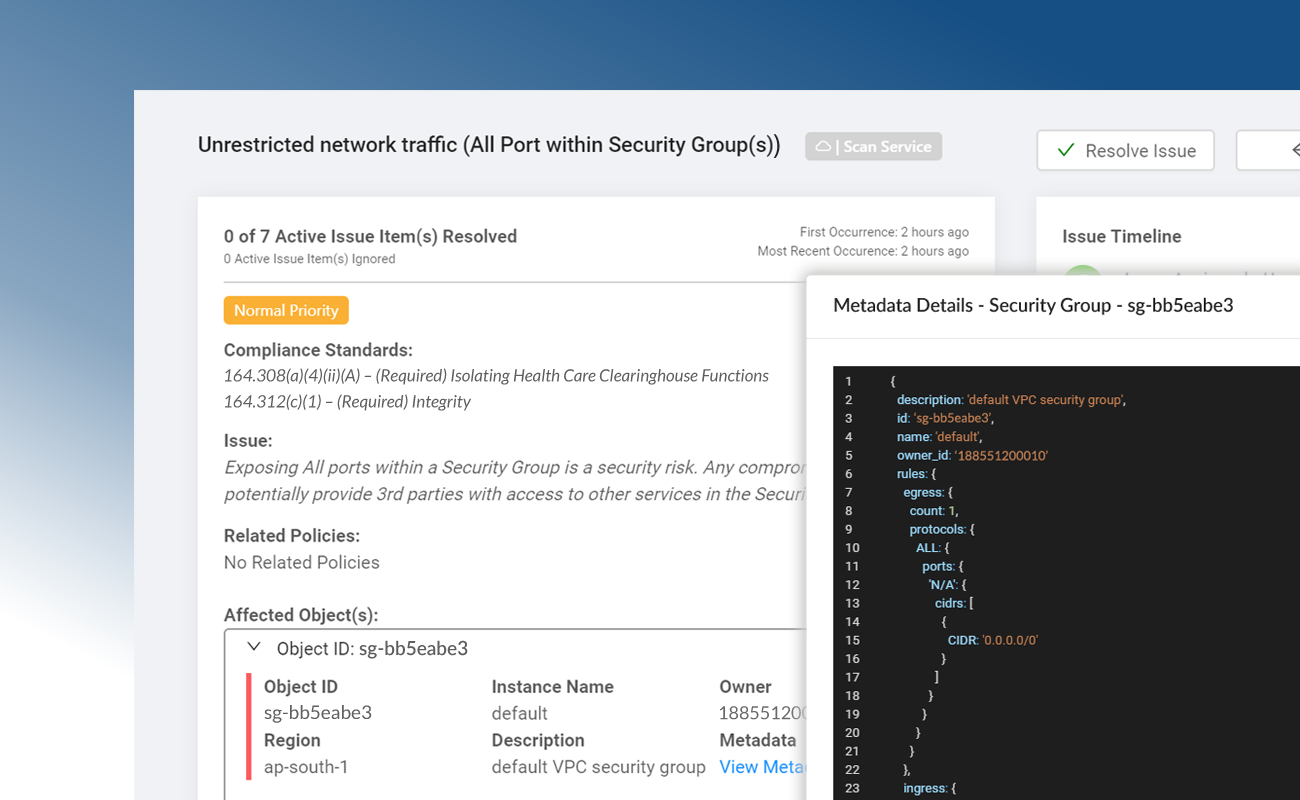
Teams with public cloud infrastructure should define logical access controls using services such Identity Access Management (IAM) and VPCs, Security Groups and Firewall Rules, as well as setting encryption settings for individual cloud resources. Teams can enforce all logical access control requirements through Dash ComplyOps security monitoring.
CC7.0: System Operations – CC7.0 defines requirements for finding system vulnerabilities, responding to security incidents, and resolving security concerns.
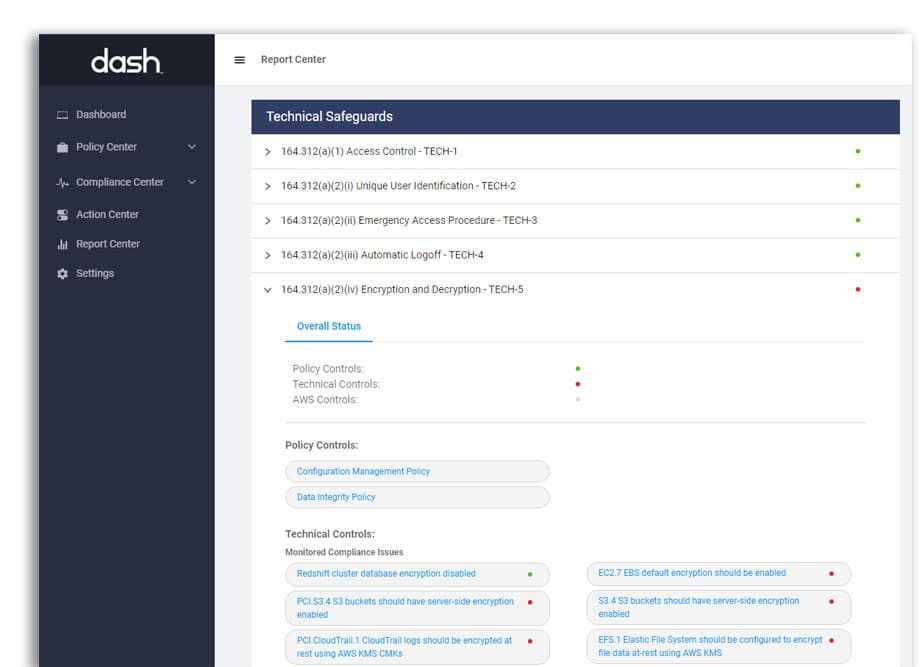
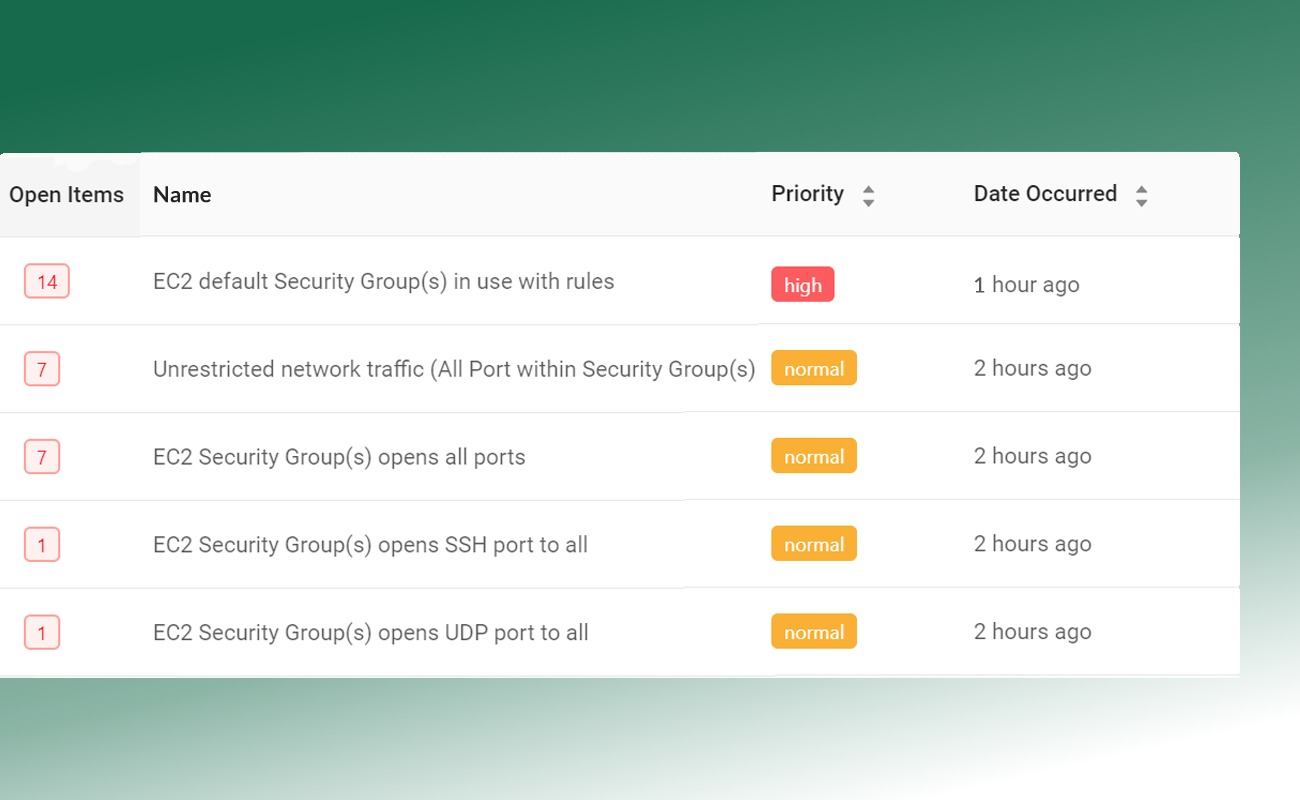
Teams should implement cloud solutions vulnerability scanning, intrusion detection and audit logging and develop Vulnerability Scanning and Incident Response Policies. Teams may consider enabling audit logging with Cloudwatch and detecting suspicious network activity with GuardDuty. Dash ComplyOps can ensure that these security solutions are properly enabled across cloud resources.
CC8.0: Change Management – CC8.0 defines requirements for setting baseline system configuration and managing changes to software and systems.
Teams should create a set of baseline cloud security controls with a tool such as Dash ComplyOps and continue to monitor cloud resources for changes to security settings and overall configuration. Dash continuous compliance monitoring can automate this process.