Continuous Compliance Monitoring
Automate security controls and compliance monitoring in the public cloud
Tour Dash ComplyOps:
Advanced Compliance Automation
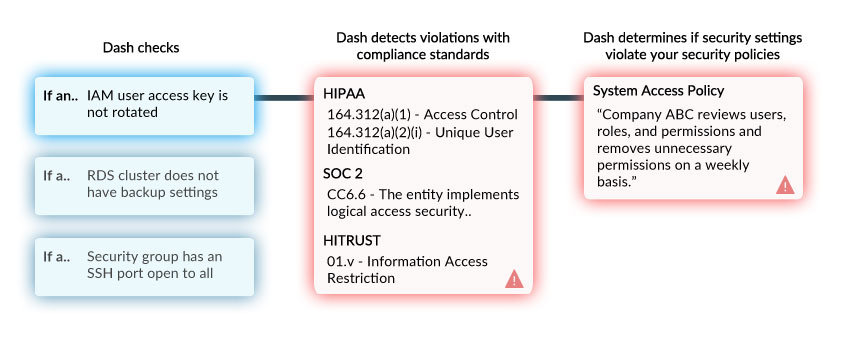
Dash continuous compliance monitoring automatically scans your IT infrastructure for security issues related to compliance standards including HIPAA, SOC 2, and NIST 800-53. Utilize Dash to execute on your security program and ensure compliance in the public cloud.
Policy Driven Compliance
Create administrative policies and controls by answering plain-English questions.
Automated Security Controls
Set technical security controls across all of your AWS cloud services.
Scan Across Your Cloud Services
Dash continuously scans and monitors all of your AWS cloud services.
Setup Continuous Compliance Monitoring In Your AWS Environment
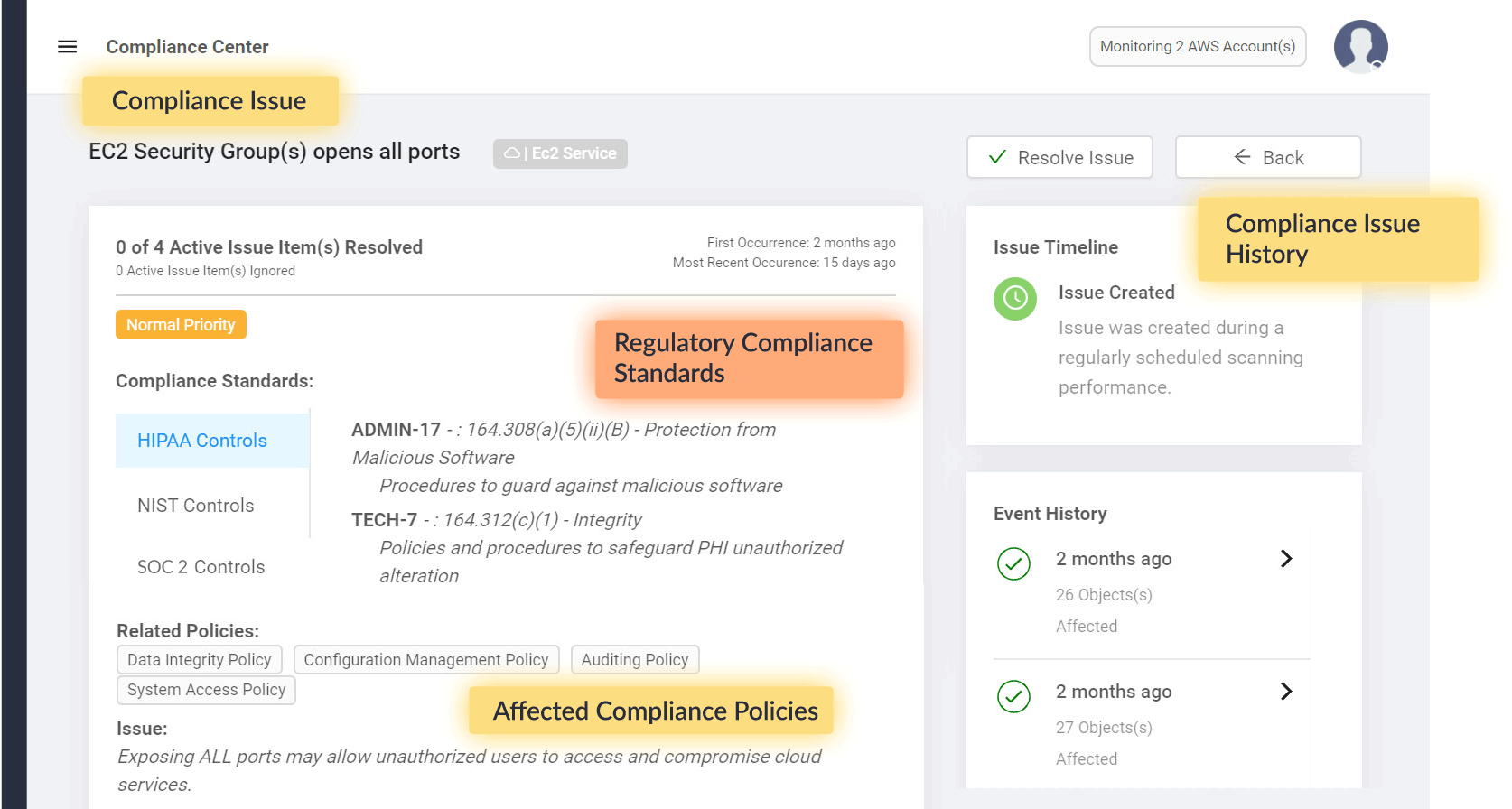
Identify & Resolve Compliance Issues
See your current state of compliance. Easily monitor and detect security and compliance issues across your cloud environments.
Detect cloud security and compliance issues including:
- Networking Issues
- Backup and Disaster Recovery
- Encryption Settings
- AWS Covered Services
- Audit Log Management
- Policy & Administrative Issues
Example Scanning & Controls
Dash configures, monitors, and remediates compliance issues within your organization’s cloud services. Below are some examples of HIPAA and SOC 2 security controls that are enforced and monitored across cloud services:
Amazon EC2
Unencrypted EBS Volumes – 164.312(a)(2)(iv) Encryption and Decryption
Security Groups With All Ports Open To Public – 164.312(c)(1) Integrity + 164.312(e)(1) Transmission Security
Security Group Allows Unrestricted Network Traffic – 164.312(c)(1) Integrity + 164.312(e)(1) Transmission Security
Security Groups Opens DB Ports To Public – 164.312(c)(1) Integrity
Security Groups Opens SSH, FTP, SMTP Ports To Public – 164.312(c)(1) Integrity
Amazon IAM
Root Account In Use – 164.312(a)(2)(i) Unique User Identification
Password Reuse Is Allowed – 164.308(a)(5)(ii)(D) Password Management
Password Standards Are Insecure – 164.308(a)(5)(ii)(D) Password Management
User Access Keys Rotation Is Disabled – 164.312(a)(1) Access Control
IAM Inline Policies Are In Use – 164.312(c)(1) Integrity + 164.312(e)(2)(i) Integrity Controls
IAM NotActions Are In Use – 164.312(c)(1) Integrity
IAM AssumeRole Is Misconfigured – 164.312(c)(1) Integrity
Amazon S3
S3 Bucket Does Not Have Encryption Enabled – 164.312(a)(2)(iv) Encryption and Decryption
S3 Bucket Does Not Have Versioning Enabled – 164.308(a)(7)(ii)(A) Data Backup Plan
S3 Bucket Does Not Have Logging Enabled – 164.312(b) Audit Controls
S3 Bucket Is Readable By All (Public) – 164.312(d) Person or Entity Authentication
S3 Bucket Is Writable By All (Public) – 164.312(d) Person or Entity Authentication
Additional services and scans included in Dash ComplyOps.
Amazon EC2
Unencrypted EBS Volumes – CC6.6 Protect Against Threats From Outside Sources + PI1.5 Protects Stored Items
Security Groups With All Ports Open To Public – CC6.6 Protect Against Threats From Outside Sources + PI1.5 Protects Stored Items
Security Group Allows Unrestricted Network Traffic –CC6.6 Protect Against Threats From Outside Sources + PI1.5 Protects Stored Items
Security Groups Opens DB Ports To Public – CC6.6 Protect Against Threats From Outside Sources + PI1.5 Protects Stored Items
Security Groups Opens SSH, FTP, SMTP Ports To Public – CC6.6 Implements Logical Access Security + PI1.5 Protects Stored Items
Amazon IAM
Root Account In Use – CC6.1 Restricts Logical Access
Password Reuse Is Allowed – CC6.2 Controls Access Credentials to Protected Assets
Password Standards Are Insecure – CC6.2 Controls Access Credentials to Protected Assets
User Access Keys Rotation Is Disabled – CC6.1 Restricts Logical Access + CC6.2 Controls Access Credentials to Protected Assets
IAM Inline Policies Are In Use – CC6.1 Restricts Logical Access + CC6.2 Controls Access Credentials to Protected Assets
IAM NotActions Are In Use – CC6.3 Entity Authorizes Based on Roles/Responsibilities + CC6.6 Protect Against Threats From Outside Sources
IAM AssumeRole Is Misconfigured – CC6.3 Entity Authorizes Based on Roles/Responsibilities + CC6.6 Protect Against Threats From Outside Sources
Amazon S3
S3 Bucket Does Not Have Encryption Enabled – CC6.1 Restricts Logical Access/Uses Encryption To Protect Data
S3 Bucket Does Not Have Versioning Enabled – A1.2 Performs Data Backup
S3 Bucket Does Not Have Logging Enabled – CC7.2 Monitors System Components
S3 Bucket Is Readable By All (Public) – CC6.1 Restricts Logical Access
S3 Bucket Is Writable By All (Public) – CC6.1 Restricts Logical Access
Additional services and scans included in Dash ComplyOps.