ISO 27001 Compliance Automation
Build and achieve ISO 27001 certification. Quickly prepare for and pass security audits, set cloud controls, and validate security efforts for customers and partners.
Book A Demo
Get Started with Dash ComplyOps compliance automation
Acheive ISO 27001 Compliance
The ISO/IEC 27000 family of standards provides organizations with a framework for securing information assets. Many enterprises and organizations in regulated industries utilize ISO 27001 standards and ISO requirements around data management and information security management system (ISMS). Enterprises often look for vendors to have implemented ISO 27001 standards or comparable cybersecurity framework.
Under the cloud shared responsibility model, Amazon Web Services (AWS) provides attestations for several ISO 27000 Standards. However, cloud customers are not automatically ISO certified by association, and must implement additional security controls. It is up to the cloud customer to implement administrative and technical security controls including security configuration around encryption, audit logging, backup and disaster recovery (DR).


Custom Compliance Policies
ISO 27001 and ISO 27002 requires that organizations set security policies and procedures around risk assessment, security objectives, and data security controls. Dash enables teams to generate custom compliance policies based around on your organization’s needs, structure, and technologies. Policies are designed around Amazon Web Services and customized through easy to answer questions.
Learn More About Administrative Policies
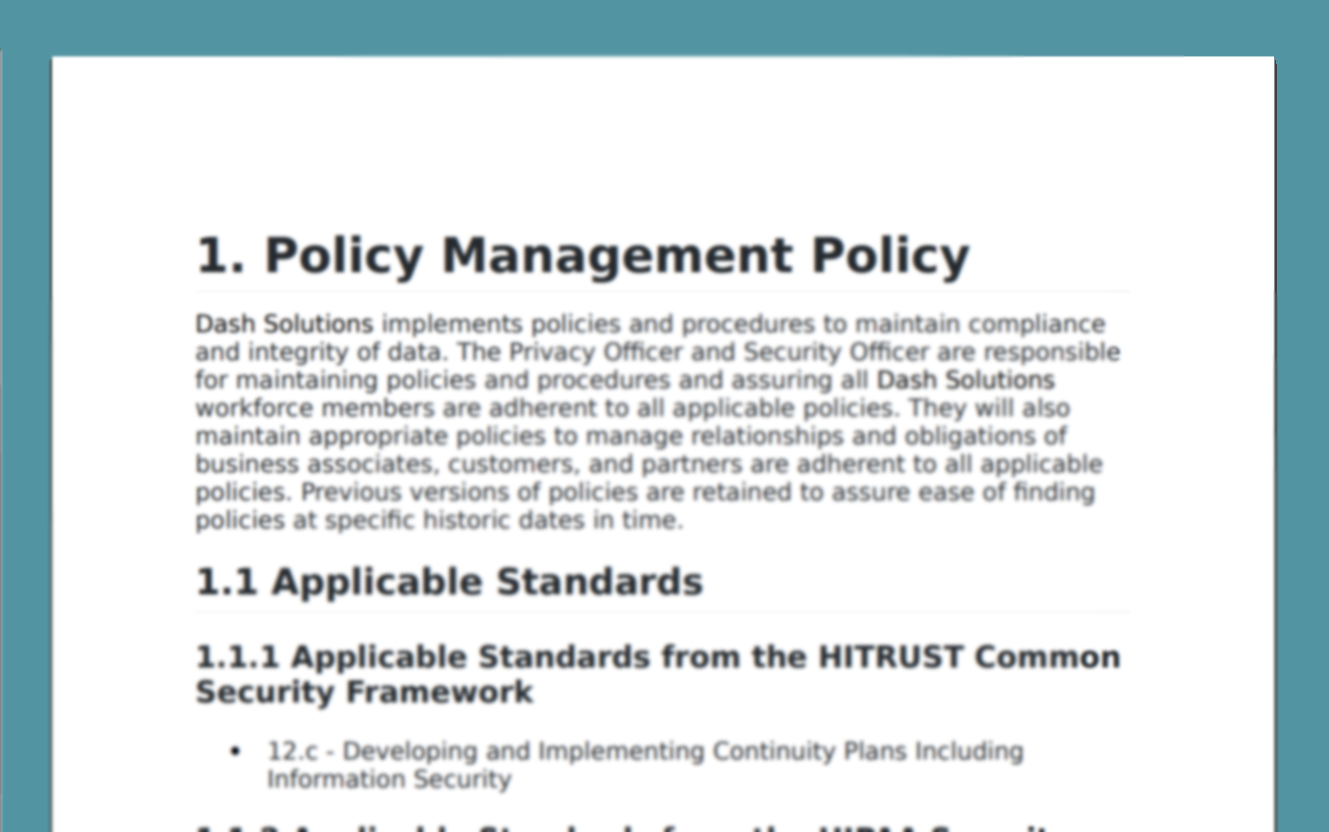
ISO 27002 Technical Security Controls
Dash establishes a set of ISO 27002 technical controls based around your organization’s established policies and procedures. Security controls are built around individual AWS cloud services, best security practices, and ISO 27001 guidance and data security standards. Organization can utilize Dash “click-to-fix” remediations to resolve compliance issues with one click and maintain technical security standards.
Learn More About Technical Controls
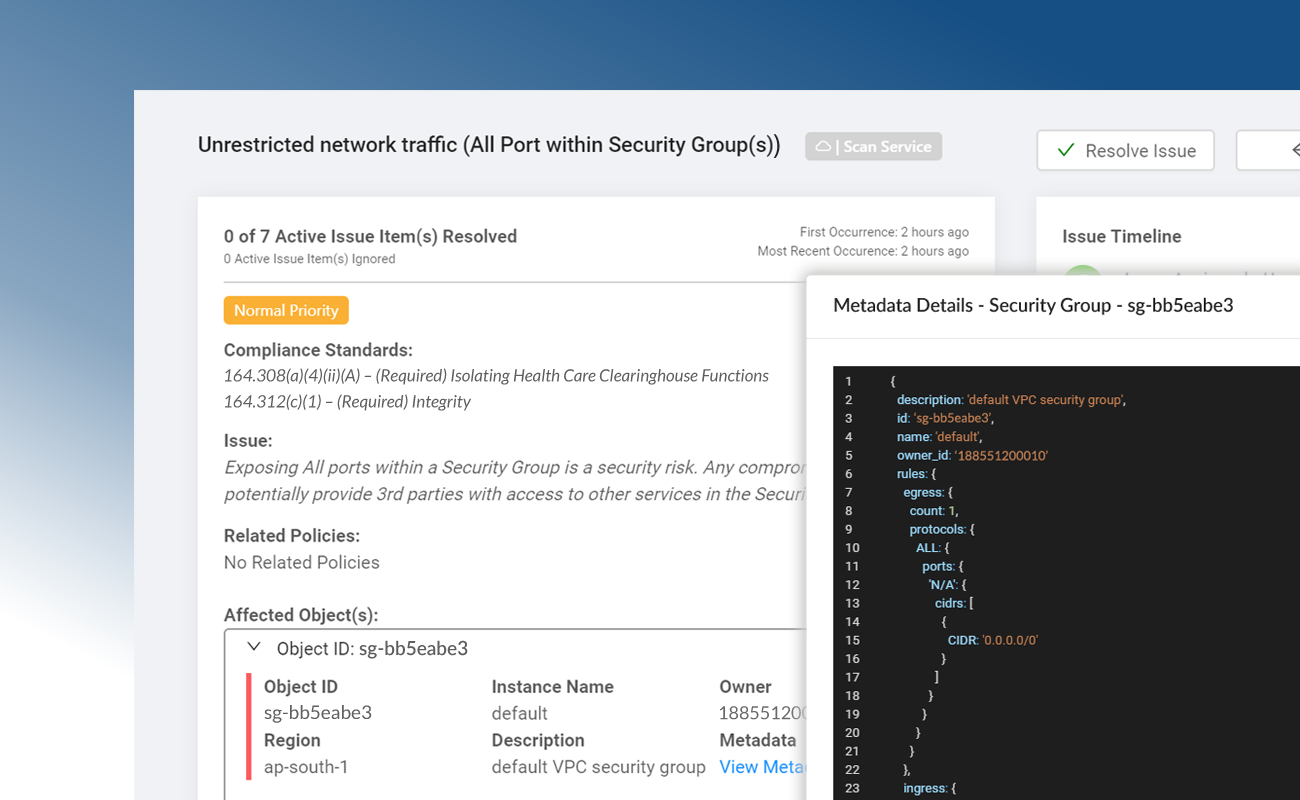
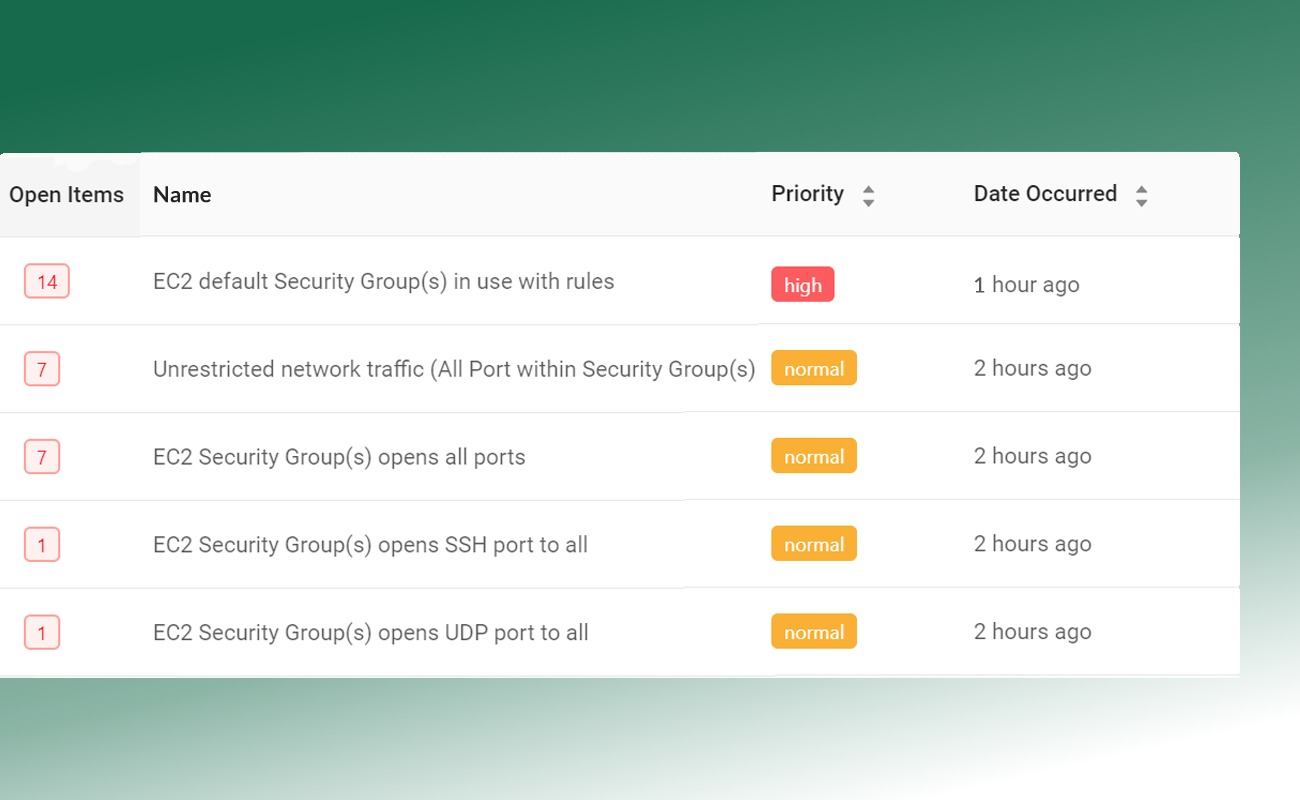
Continuous Compliance Monitoring
Dash continuously monitors your AWS accounts for ISO compliance issues. Dash detects compliance concerns in your cloud environment such as unencrypted EBS volumes, audit logging issues and S3 buckets that are open to the public, alerts your team, and provides steps for resolving issues before they become full-blown violations.
Learn More About Continuous Compliance Monitoring
Get Started With AWS ISO 27001 Automation.
Address ISO 27000 Series Standards In AWS
Dash enables teams to implement the ISO 27000 family of security controls. These standards help organizations manage data security within the organization.
ISO 27001 – Security Controls
ISO 270001 provides a framework of policies, procedures, and controls involved in for developing an information security management system (ISMS). This includes performing risk assessment, setting objectives and controls to implement.
ISO 27002 – Information Technology | Security Techniques
ISO 27002 provides hundreds of potential controls and security mechanisms to be implemented alongside ISO 27001. Controls include security policies, asset management, access control, cryptography, and operations security.
ISO 27017 – Cloud Specific Controls
ISO 27017 provides guidance on implementing security standards around cloud computing, and cloud specific information security controls that supplement ISO 27001.
ISO 27018 – Personal Data Protection
ISO 27018 provides controls applicable to public cloud Personally Identifiable Information (PII). It also provides a set of additional controls and associated guidance to address public cloud PII protections not addressed by other ISO 27000 standards.
Manage ISO 27001 Compliance in AWS
Prepare For ISO 27001 Certification
Dash enables teams to plan and implement compliance safeguards and security controls including the following
Data Protection and Privacy
Dash security policies dictate user roles, responsibilities, processes, and management of personally identifiable data and system access.
Availability and Continguency Planning
Dash provides policies around cloud service availability, backup and disaster recovery (DR), to ensure that production services and data are always accessible.
Regulatory Compliance
Dash procedures and processes enable teams to manage and monitor regulatory compliance, and mitigate regulatory compliance risk.
Continuous Security Monitoring
Dash Continuous Compliance Monitoring ensures that cloud resources have secure configuration, and alerts teams of compliance vulnerabilities.
Identity Management and Access Control
Dash security controls, together with AWS Identity Access Management (IAM) restrict system access to only authorized users, roles, and applications. Services access is restricted to avoid unauthorized access.
Data Integrity
Dash confirms that AWS services are configured with proper protections including networking, encryption, and backup. Safeguards are implemented to protect the confidentiality, integrity, and availability of information.
Want To Learn More About Compliance Automation?
Ready To Get Started With Dash ComplyOps?
Dash ComplyOps
AWS Security Automation
Dash ComplyOps empowers teams to configure, monitor, and maintain robust security controls across AWS cloud environments.
7-day risk free trial.
7-day risk free trial